How to Boost your Organization’s Ransomware Protection and Prevent Attacks

Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Ransomware is surging in 2025—and no organization is safe. Cybercriminals are behind nearly half of all cyberattacks in the past year, and ransomware gangs alone have claimed 6,133 victims, a 14% increase from 2023, according to the 2025 LUMINAR Threat Landscape Report. These attacks are no longer just about locking files—they now combine encryption with extortion, exposing sensitive data and triggering financial losses, reputational damage and regulatory penalties. With human error driving 60% of breaches, often via phishing or social engineering, untrained employees are prime targets. To stay ahead of these evolving threats, organizations must adopt a proactive multi-layered defense strategy. This article shares the most effective approaches to ransomware protection that you can start implementing today.
What is Ransomware?
Ransomware is a particularly dangerous form of malware designed to block access to a system or data, usually by encrypting it, until the victim pays a ransom. Often masquerading as legitimate files or links, ransomware finds its way into an organization’s network and systems through social engineering tactics, most notably phishing emails. These emails trick users into clicking malicious links or downloading infected attachments, opening the door for attackers to gain control of sensitive data.
Once ransomware takes hold, it can spread rapidly across networks, locking files and demanding payment, typically in cryptocurrency, to restore access. However, paying the ransom does not guarantee data recovery. Victims are dealing with cybercriminals, and there’s no assurance that the decryption key will be provided or that attackers haven’t already copied or leaked the data elsewhere.
The Ransomware Landscape
Ransomware remains a top global cyber threat, accounting for 49% of all cyberattacks in 2024 according to the 2025 LUMINAR Threat Landscape Report. The average ransomware payment is a staggering $850,700, with total losses per ransomware attack, including downtime and recovery costs, often surpassing $4.9 million. These alarming figures highlight the urgent need for proactive defense strategies that include multi-factor authentication, employee training, endpoint protection, regular backups and external threat intelligence.
The ransomware ecosystem continues to evolve, with 44 new groups surfacing in 2024 and 20 more already appearing in 2025, spurred in part by global law enforcement takedown campaigns like Operation Cronos, which targeted LockBit in early 2024. Although LockBit was not fully dismantled, the vacuum it left created a void for other ransomware groups to emerge and grow. Meanwhile, Ransomware-as-a-Service (RaaS) operations are expanding with white-label models, enabling less technical affiliates to run attacks using established infrastructure for a share of the ransom. Still, the landscape remains volatile with groups frequently vanishing and rebranding to evade law enforcement or conduct exit scams, reflecting both the adaptability and instability of the ransomware underground.
Common Types of Ransomware and the Rise of Ransomware-as-a-Service
Ransomware attacks have evolved rapidly in both technique and complexity. While the overarching goal remains the same, to encrypt critical data and demand a ransom for its release, the delivery methods, malware structures and motivations behind these attacks vary. Below are the most common ransomware types, followed by a deep dive into one of the most significant developments in recent years: Ransomware-as-a-Service (RaaS).

- Crypto Ransomware (Encryptors): Encrypts a victim’s files and demands payment in exchange for the decryption key.
- Lockers: Locks users out of their devices entirely, displaying ransom messages without necessarily encrypting files.
- Scareware: Poses as legitimate security software, using fake alerts to trick users into paying for false threats.
- Doxware (Leakware): Threatens to leak sensitive or compromising data unless the ransom is paid.
Ransomware-as-a-Service (RaaS): Industrializing Cybercrime
What is RaaS?
Ransomware-as-a-Service (RaaS) is a subscription-based business model in which ransomware developers lease out their malware to affiliates who execute the attacks. This model has revolutionized the ransomware landscape, making it easier than ever for even unskilled threat actors to launch sophisticated attacks.
RaaS operators provide everything needed for an attack, including the ransomware payload, distribution platform, payment processing (often in cryptocurrency) and sometimes even customer support for victims. In exchange, they take a cut of the ransom payment, typically between 30–40%.
This model enables specialization:
- Operators focus on refining malware and managing the backend infrastructure.
- Affiliates handle social engineering, system penetration and spreading the ransomware.
Because it lowers the technical barrier to entry, RaaS has significantly fueled the global surge in ransomware attacks, turning isolated hacking groups into sprawling cybercrime ecosystems.
Ransomware is no longer just the product of a lone hacker. It’s now a multi-million-dollar industry fueled by a global black market. The RaaS model has democratized access to powerful malware and blurred the line between developers and attackers. To stay ahead, organizations must adopt a layered defense strategy that combines next-gen security tools, continuous monitoring and end-user education.
How Ransomware Infiltrates: Common Infection Vectors
Ransomware attacks are not brute-force cyber assaults, they’re often the result of well-orchestrated infiltration strategies. Threat actors leverage a range of entry points to breach IT environments, deploy malware and spread it across systems. Understanding how ransomware gains entry is critical to preventing its spread. Here are the top methods threat actors use:
- Credential theft and account compromise: Attackers use stolen or weak credentials to access systems, disable defenses and deploy ransomware across the network.
- Phishing attacks: Phishing was the initial access point in 41% of ransomware cases in 2024, typically delivered through deceptive emails with malicious links or attachments.
- Exploitation of software vulnerabilities: Attackers exploit unpatched software flaws to inject ransomware without user interaction, often targeting outdated systems.
- Malware masquerading as legitimate software: Ransomware often disguises itself as trusted apps or updates and is frequently deployed through compromised Remote Desktop Protocol (RDP) access.
- Compromised websites and malicious ads: Users can unknowingly download ransomware by visiting compromised sites or clicking on infected ads in a tactic known as drive-by downloading.
How Can Organizations Protect Themselves from Ransomware?
Ransomware attacks are increasingly sophisticated, exploiting both technical flaws and human behavior. To stay protected, organizations need a multi-layered defense that combines user education, strict access controls, regular patching and advanced external threat intelligence.
These key practices can help reduce the risk and impact of ransomware:
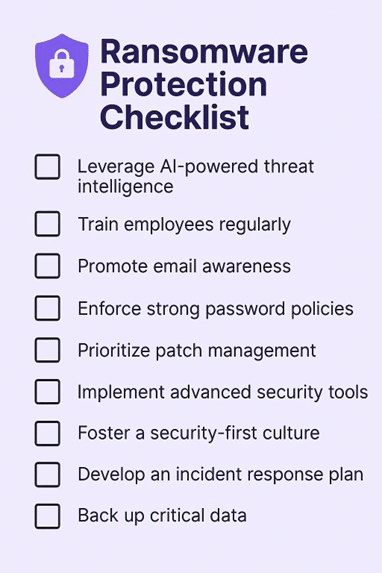
- Leverage AI-powered threat intelligence: Use external threat intelligence solutions enhanced with GenAI to stay ahead of evolving ransomware tactics, techniques and procedures (TTPs) and receive tailored, real-time threat assessments.
- Train employees regularly: Educate staff on phishing recognition, malware identification and safe digital behavior through interactive training and simulations.
- Promote e-mail awareness: Instruct employees to scrutinize email content and attachments, report suspicious messages and avoid enabling macros in unknown documents.
- Enforce strong password policies: Require unique, complex passwords and use multifactor authentication (MFA) to prevent unauthorized access.
- Prioritize patch management: Keep systems and applications up to date and conduct regular vulnerability scans to close known security gaps.
- Implement advanced security tools: Use antivirus software, intrusion detection systems (IDS) and virtual private networks (VPNs) to protect against threats at multiple levels.
- Foster a security-first culture: Encourage continuous learning, simulate phishing scenarios and promote cybersecurity awareness at all levels of the organization.
- Develop an incident response plan: Establish clear steps for containing ransomware, reporting incidents and communicating during an attack.
- Back up critical data: Perform regular backups, store them securely and ensure they’re isolated from the primary network to prevent compromise.
This approach not only strengthens cyber defense but also improves an organization’s ability to proactively detect, respond to and recover from ransomware attacks.
The Importance of Ransomware Monitoring and Protection
As ransomware threats escalate in both volume and complexity, organizations must move beyond traditional defensive strategies and adopt real-time monitoring fortified by AI-powered external threat intelligence. While basic preventive measures remain important, they often fall short against rapidly evolving tactics. Continuous monitoring, fueled by intelligent external threat feeds, can identify early indicators of compromise such as anomalous encryption activity or unauthorized access. This enables swift detection and automated containment before ransomware can cause widespread damage.
AI-powered external threat intelligence solutions are pivotal in this landscape, combining robust patch management with continuous monitoring and real-time threat visibility. These solutions help organizations keep systems secure and up to date while raising awareness and providing actionable insights that allow them to stay ahead of ransomware attacks. By incorporating these tools into their security posture, organizations move from reactive defense to a proactive intelligence-driven strategy that enhances resilience and enables faster, more coordinated incident response.
How to Choose an External Threat Intelligence Solution for Ransomware Protection
With ransomware tactics becoming more targeted and adaptive, selecting the right external threat intelligence solution is critical to reducing risk and staying ahead of attackers. The ideal platform should do more than provide raw data. It must offer contextualized insights, seamless integration and proactive risk reduction capabilities. Here’s what to look for when evaluating solutions:
- Comprehensive Threat Visibility
A robust solution should provide access to a wide range of sources, including ransomware data leak sites (DLS) on the dark web. This visibility allows organizations to track ransomware campaigns in real time and detect early indicators of targeted attacks. For example, LUMINAR, Cognyte’s AI-powered external threat intelligence solution, includes extensive dark web and commercial feed coverage, as well as a proprietary database with historical data, helping teams investigate threats even after surface content has been removed. LUMINAR also automatically assigns risk levels to intelligence related to ransomware attacks, enabling security teams to quickly prioritize and respond to the most pressing threats with targeted mitigation efforts.
 Ransomware group intelligence provided via LUMINAR’s Threat Actor Profiling Module
Ransomware group intelligence provided via LUMINAR’s Threat Actor Profiling Module- Real-Time, Actionable Intelligence
Look for platforms that issue timely alerts on ransomware activities and share detailed intelligence on threat actors’ tactics, techniques and procedures (TTPs). LUMINAR delivers imminent ransomware alerts paired with rich intelligence, equipping security teams with the context needed to anticipate and disrupt attacks before they escalate. - Seamless Integration with Existing Tools
An effective external threat intelligence solution should easily integrate with security orchestration, automation and Response (SOAR), security information and event management (SIEM) and other security systems to operationalize threat data. For example, LUMINAR supports automated extraction and delivery of indicators of compromise (IOCs) that integrate effortlessly with leading endpoint detection and response (EDR), SOAR and SIEM platforms, streamlining the workflow from detection to response. - Deep Investigation and Cross-Platform Visibility
Effective protection requires the ability to investigate threats across platforms and correlate disparate data points. LUMINAR enables detailed investigations into cybercriminal group activities across multiple platforms. This holistic visibility empowers analysts to connect the dots between disparate data points and uncover the full extent of a campaign. - Proactive Vulnerability Management
Preventing ransomware also means closing security gaps before they’re exploited. Solutions should include modules for vulnerability intelligence and external attack surface management (EASM). LUMINAR’s integrated EASM and Vulnerability Intelligence Modules help prioritize patching and alert teams to actively exploited vulnerabilities, supporting faster remediation and stronger ransomware defenses.
Conclusion
Preventing ransomware attacks requires a multi-layered approach, including employee training, email vigilance, strong password policies, advanced security measures, fostering a cybersecurity awareness culture and advanced cybersecurity systems, including an external threat intelligence solution. By implementing an incident response plan, backing up critical data and using threat intelligence, organizations can strengthen security and reduce ransomware risks.
Learn more about how LUMINAR can protect your organization from ransomware threats
The post How to Boost your Organization’s Ransomware Protection and Prevent Attacks appeared first on Cognyte.
Article Link: How to Protect Against Ransomware Attacks Effectively | Cognyte
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics

