Russian ‘Laundry Bear’ Hackers Breach Dutch Police Using Infostealers
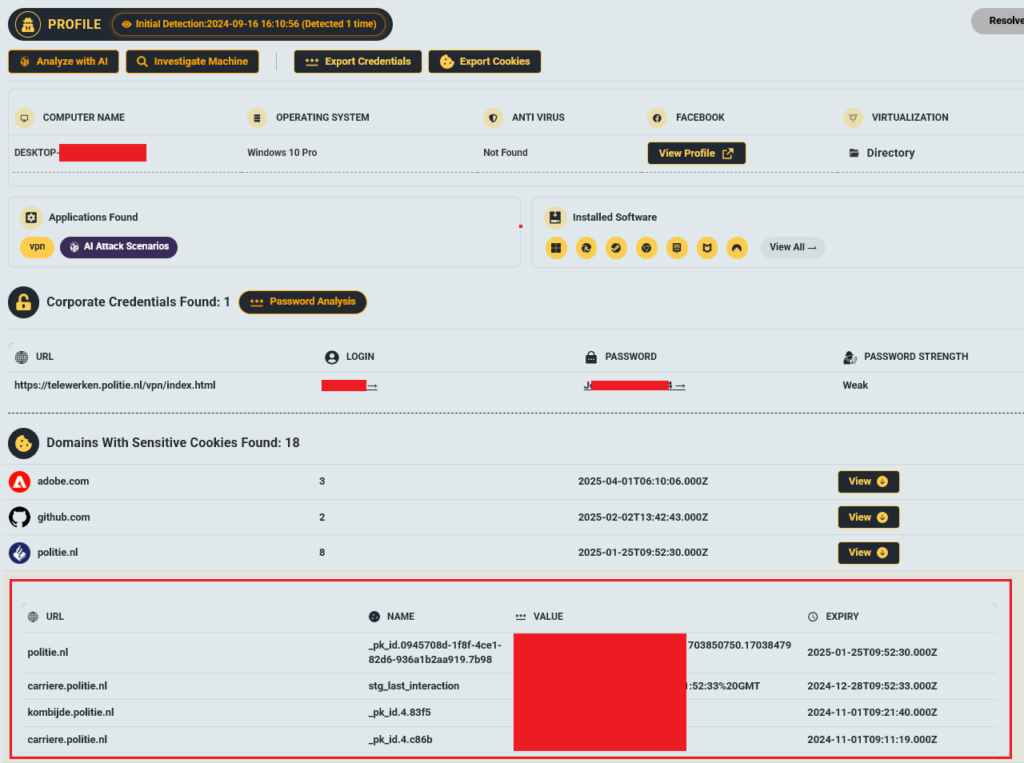
A new Russian hacking group, “Laundry Bear” (aka “Void Blizzard”), breached the Dutch police in October 2024, stealing contact details of thousands of officers. The attack, highly likely linked to a September 12, 2024, infostealer infection of a police employee, compromised VPN credentials and politie.nl session cookies, enabling a pass-the-cookie attack. Hudson Rock data confirms the infection, highlighting the preventable nature of this cyberespionage operation.
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Laundry Bear’s Infostealer-Driven Espionage
Active since April 2024, Laundry Bear targets critical sectors in NATO states and Ukraine, focusing on government, defense, and healthcare. Microsoft and Dutch intelligence (AIVD/MIVD) note the group’s use of stolen credentials, likely bought from dark web markets, and spear-phishing with typosquatted domains like “micsrosoftonline[.]com.” Unlike destructive Russian groups, Laundry Bear prioritizes data theft, abusing cloud APIs to harvest emails and files.
Dutch Police Breach: A Preventable Failure
The Dutch police breach began with an infostealer that stole session cookies, allowing Laundry Bear to bypass authentication and access the network. This mirrors a growing trend: state-sponsored actors leveraging infostealers for high-impact attacks. Basic defenses like multi-factor authentication (MFA), short-lived session tokens, and employee training could have prevented this incident.
A Global Threat
Laundry Bear’s campaign extends beyond the Netherlands, targeting Ukrainian and Western organizations to gather intelligence on military aid and sanctioned technologies. The group’s reliance on infostealers underscores their accessibility to sophisticated actors, amplifying the threat.
Stopping the Infostealer Threat
Organizations can mitigate infostealer risks by:
- Enforcing phishing-resistant MFA
- Monitoring for infostealer activity with endpoint detection
- Shortening session token lifespans
- Training employees to spot phishing
- Auditing third-party access
Conclusion
The Dutch police breach exposes how infostealers empower groups like Laundry Bear to infiltrate critical systems. This preventable attack, driven by a single infection on September 12, 2024, calls for urgent action to counter the infostealer epidemic.
To learn more about how Hudson Rock protects companies from imminent intrusions caused by info-stealer infections of employees, partners, and users, as well as how we enrich existing cybersecurity solutions with our cybercrime intelligence API, please schedule a call with us, here: https://www.hudsonrock.com/schedule-demo
We also provide access to various free cybercrime intelligence tools that you can find here: www.hudsonrock.com/free-tools
Thanks for reading, Rock Hudson Rock!
Follow us on LinkedIn: https://www.linkedin.com/company/hudson-rock
Follow us on Twitter: https://www.twitter.com/RockHudsonRock
The post Russian ‘Laundry Bear’ Hackers Breach Dutch Police Using Infostealers appeared first on InfoStealers.
Article Link: Russian ‘Laundry Bear’ Hackers Breach Dutch Police Using Infostealers | InfoStealers
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics
