How CVE-2025-6018 and CVE-2025-6019 Enable Full Root Access on Linux
How CVE-2025-6018 and CVE-2025-6019 Enable Full Root Access on Linux
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Two newly uncovered Local Privilege Escalation (LPE) vulnerabilities, CVE-2025-6018 and CVE-2025-6019, could allow attackers to chain low-level access into full root control on several Linux distributions. These flaws affect openSUSE Leap 15, SUSE Linux Enterprise 15, and systems running the widely-deployed udisks daemon.
CVE-2025-6018: Exploiting PAM to Masquerade as a Physical User
In the first vulnerability, an unprivileged user connecting via SSH can manipulate how environment variables are interpreted during login on SUSE systems. Due to a permissive configuration in the pam_env module (enabled by default in Linux-PAM 1.3.0), arbitrary environment variables from a user’s ~/.pam_environment file are processed early in the login flow.
This flaw allows the attacker to spoof variables like XDG_SEAT and XDG_VTNR, which are later used by the pam_systemd module to determine the session’s physical context. As a result, the remote attacker can impersonate a local “active” user, gaining permission to perform actions typically reserved for someone physically at the machine.
For example, a remote user who injects these variables may suddenly be granted the ability to reboot or suspend the system via polkit, effectively blurring the line between remote and physical access.
CVE-2025-6019: Root Access via XFS Resize in libblockdev
The second vulnerability targets the udisks daemon and libblockdev, which manage storage devices on many Linux distributions. Here, an “allow_active” user (either legitimate or impersonated using CVE-2025-6018) can gain root access by abusing how XFS file systems are resized.
During the resize process, udisks uses libblockdev to mount the filesystem temporarily under /tmp. Critically, this mount is performed without enforcing nosuid or nodev options. This oversight enables an attacker to craft an XFS image with a set-user-ID root shell, mount it using the resize operation, and execute it to obtain full root privileges.
What makes this exploit especially accessible is that udisks is installed by default on many systems, and the resize capability for physical users is explicitly permitted via polkit.
Chaining Both Exploits for Full Compromise
Individually, these vulnerabilities offer a privilege step: one from remote to local physical user, the other from local physical user to root. When chained, however, they represent a complete privilege escalation path. An attacker starting with a basic unprivileged SSH account could manipulate PAM to appear as a local user and then leverage the udisks daemon to obtain root control.
Security Measures and Patch Guidance
System administrators should apply vendor patches immediately. SUSE has issued updates for both vulnerabilities, and additional guidance may be available through your Linux distribution’s security advisories.
To reduce exposure:
- Disable user_readenv in PAM configurations (pam_env), especially in /etc/pam.d/sshd
- Audit and limit polkit actions granted to “allow_active” users
- Monitor systems for unexpected loop device mounts under /tmp
The long-term fix includes removing support for user-controlled environment variables in PAM and tightening udisks mount behavior.
For complete details of CVE-2025-6018 and CVE-2025-6019, visit the original advisory here.
CVE-2023-0386: Kernel-Level Root Escalation Alert
While CVE-2025-6018 and CVE-2025-6019 expose a dangerous privilege escalation chain on SUSE systems, another kernel-level flaw is also drawing urgent attention. CISA recently alerted U.S. federal agencies to active exploitation of CVE-2023-0386 (CVSS 7.8) – a local privilege escalation vulnerability in the Linux kernel’s OverlayFS module.
The vulnerability stems from improper handling of file ownership when copying capable files across mount points. If left unpatched, it allows local attackers to escalate privileges to root.
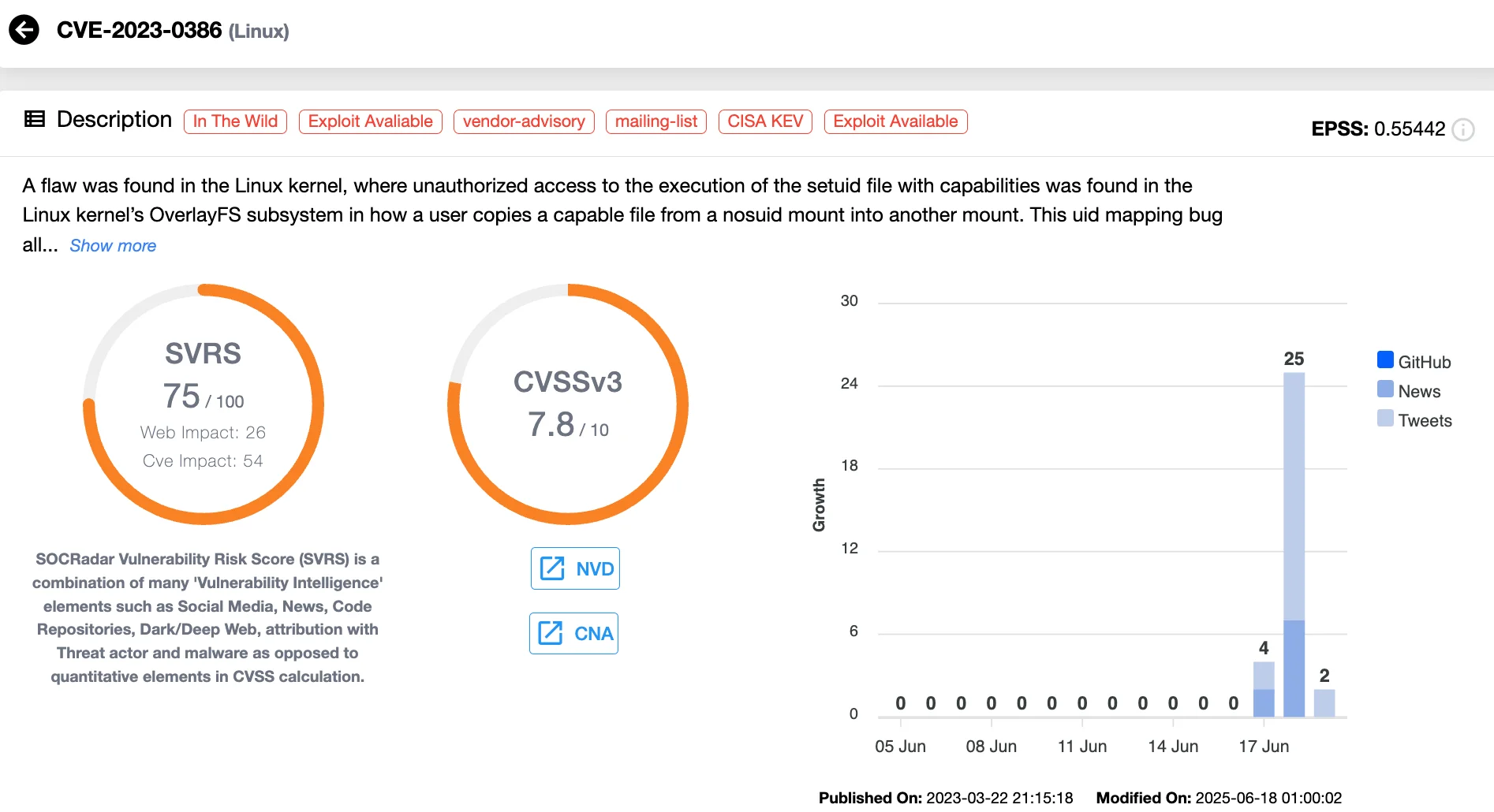
CVE-2023-0386 (SOCRadar Vulnerability Intelligence)
This issue affects a broad set of Linux distributions, including Ubuntu, Red Hat, Debian, and Amazon Linux, particularly those running kernel versions below 6.2.
Despite being patched in early 2023, the flaw remains a popular target due to the public release of exploit code and its ease of use. CISA has demanded that federal agencies patch the flaw by July 8, 2025, including it in the Known Exploited Vulnerabilities (KEV) Catalog.
As exploitation continues in the wild, this highlights the importance of timely patching; not just for newly discovered vulnerabilities, but also for older issues that remain unaddressed in many environments. To effectively reduce your exposure, it is essential to combine asset visibility with actionable intelligence.
SOCRadar’s Attack Surface Management (ASM) continuously scans your external environment to identify vulnerable systems, outdated software, and exposed services, giving your security team a clear picture of where risks lie.
Easily track new security vulnerabilities & exploit trends with SOCRadar Vulnerability Intelligence
Paired with SOCRadar’s Cyber Threat Intelligence module, which delivers updates on new vulnerabilities and active exploit trends, your team can prioritize patching efforts based on context and urgency.
Article Link: https://socradar.io/cve-2025-6018-and-cve-2025-6019-root-access-on-linux/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics

