Critical OAuth2-Proxy Vulnerability (CVE-2025-54576) Lets Attackers Bypass Authentication
Critical OAuth2-Proxy Vulnerability (CVE-2025-54576) Lets Attackers Bypass Authentication
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
A security flaw has been found in OAuth2-Proxy, a tool that helps secure web applications using OAuth2 or OIDC authentication. Tracked as CVE-2025-54576, this vulnerability has been given a CVSS score of 9.1, marking it as critical.
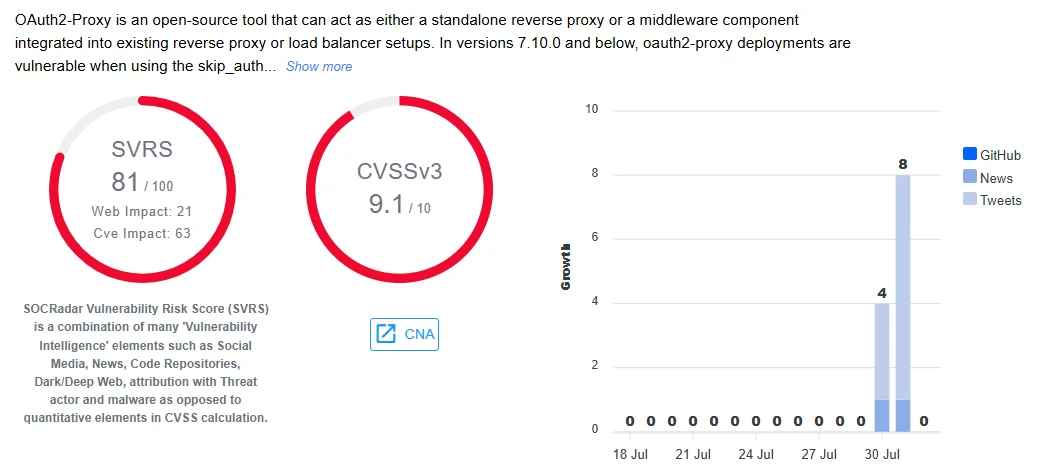
CVE-2025-54576 vulnerability details (SOCRadar Vulnerability Intelligence)
What is OAuth2-Proxy?
OAuth2-Proxy acts as a reverse proxy or middleware. It connects user requests to an OAuth2 or OIDC provider for authentication. Many developers use it with Kubernetes, load balancers, or cloud-native setups. Its flexibility and open-source nature have made it a popular choice for protecting web applications.
What’s the Issue?
The issue lies in the skip_auth_routes setting. This feature lets developers list routes that should bypass authentication, using regular expressions (regex). However, a flaw in the tool causes it to match these patterns against the full request URI, including query parameters, not just the path.
This means attackers can add special query strings to protected URLs and trick the proxy into skipping authentication.
Example
If a developer configures:
skip_auth_routes = [“^/foo/.*/bar$”]
They likely intend to allow access to URLs like:
/foo/something/bar
But due to the flaw, an attacker could gain access to something sensitive like:
/foo/critical_endpoint?param=/bar
Even though /foo/critical_endpoint is protected, the presence of ?param=/bar tricks the system into skipping authentication.
Who’s at Risk?
This bug mainly affects users who use broad or wildcard regex patterns in their skip_auth_routes setting. The risk increases if the backend service doesn’t block or check for unexpected query parameters.
Fix Available
The issue has been fixed in version v7.11.0 of OAuth2-Proxy. Users should upgrade as soon as possible.
If you can’t upgrade immediately, take these steps to reduce risk:
- Audit your configurations: Look for overly broad regex in skip_auth_routes.
- Use strict patterns: Avoid wildcards. Use exact paths when possible.
- Anchor your regex: Make sure patterns start with ^ and end with $.
- Match only the path: Strip query parameters before applying regex.
Safer example:
Instead of this:
“^/public/.*”
Use specific paths:
“^/public/assets$”, “^/public/health$”, “^/api/status$”
If you use skip_auth_routes, don’t wait. Update to version v7.11.0 now. If you can’t update yet, check your settings. Use exact paths, avoid wildcards, and make sure your rules only match what you really want.
SOCRadar’s Attack Surface Management (ASM) module: Monitor assets and company vulnerabilities
Discover hidden risks in your environment ahead of attackers. SOCRadar Attack Surface Management (ASM) scans your external assets nonstop, spotting weak points, forgotten services, and risky exposures.
Article Link: https://socradar.io/oauth2-proxy-cve-2025-54576-bypass-authentication/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics

