Florida Government Data, Binance Checker, and Legal Organization Leak Surface on Dark Web
Florida Government Data, Binance Checker, and Legal Organization Leak Surface on Dark Web
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
SOCRadar’s Dark Web Team observed multiple new listings on hacker forums this week, including alleged databases tied to government and legal organizations, unauthorized FTP access, and illicit cybercrime tools. Among them were offers for a stealer log search platform, a Binance checker tool, data allegedly from the official portal of the State of Florida, and stolen records linked to Massachusetts Prisoners’ Legal Services. Each claim reflects ongoing exposure risks across public, financial, and corporate sectors.
Receive a Free Dark Web Report for Your Organization:
Alleged Stealer Logs Service is Detected
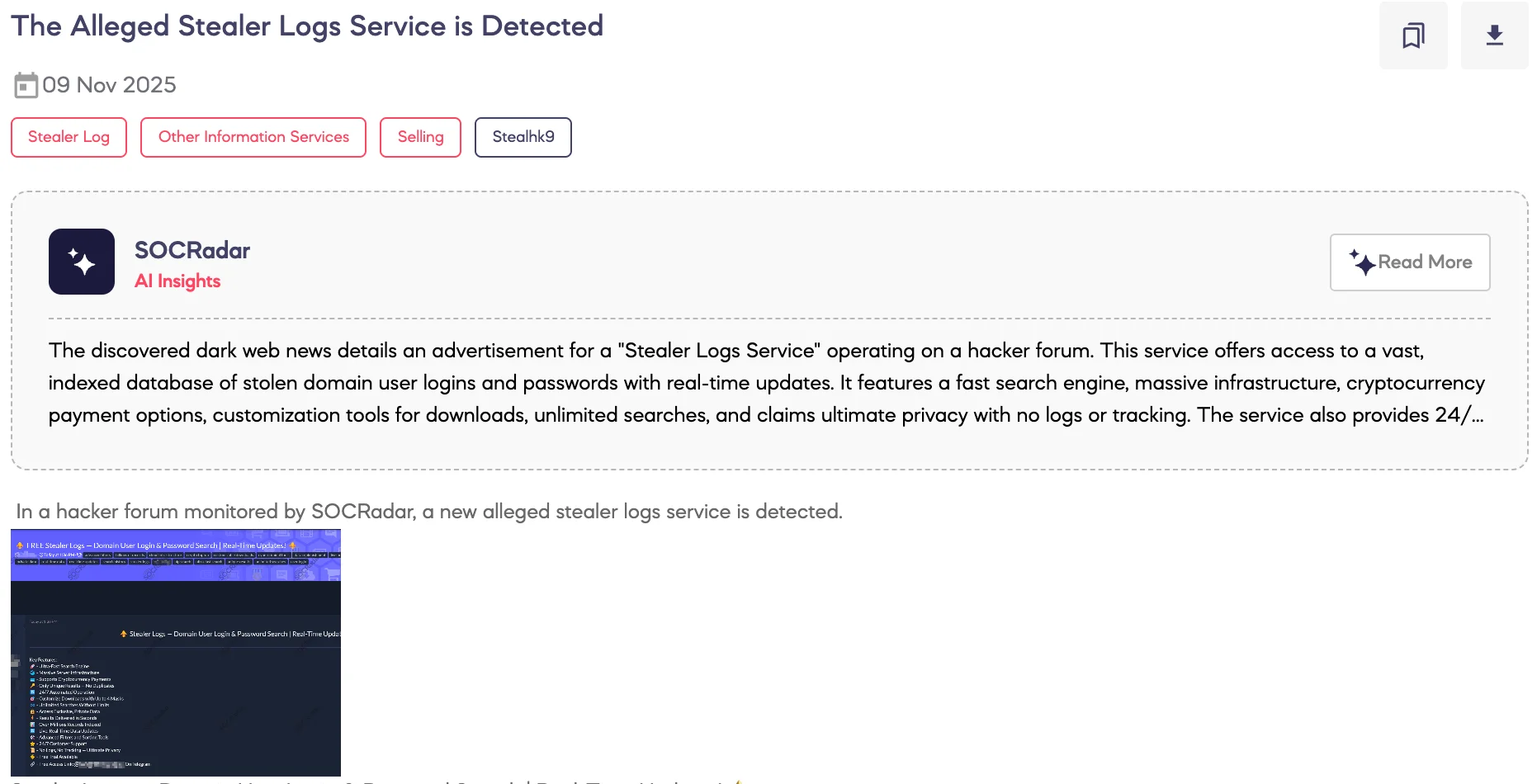
SOCRadar Dark Web Team monitored a hacker forum where a threat actor advertised a stealer logs search service. The post claims the service indexes millions of stolen records and offers an ultra-fast search engine with live updates, advanced filters, and customizable downloads. The threat actor claims unlimited searches, cryptocurrency payments, strict no-logs privacy, 24/7 support, a free trial, and a Telegram access link.
Alleged Checker Tool for Binance is on Sale

SOCRadar Dark Web Team detected on a hacker forum that a threat actor advertised a Binance checker tool for sale. The post claims the tool validates Binance phone numbers and email addresses with “live proof,” bypasses CAPTCHA, supports individual and bulk verification, and offers a free demo requiring a proxy and CAPTCHA API key. The threat actor claims API integration, escrow-backed cryptocurrency payments, lifetime access with updates, and fixed prices: $650 for the phone checker and $850 for the email checker.
Alleged Database of the Official Portal of the State of Florida is on Sale
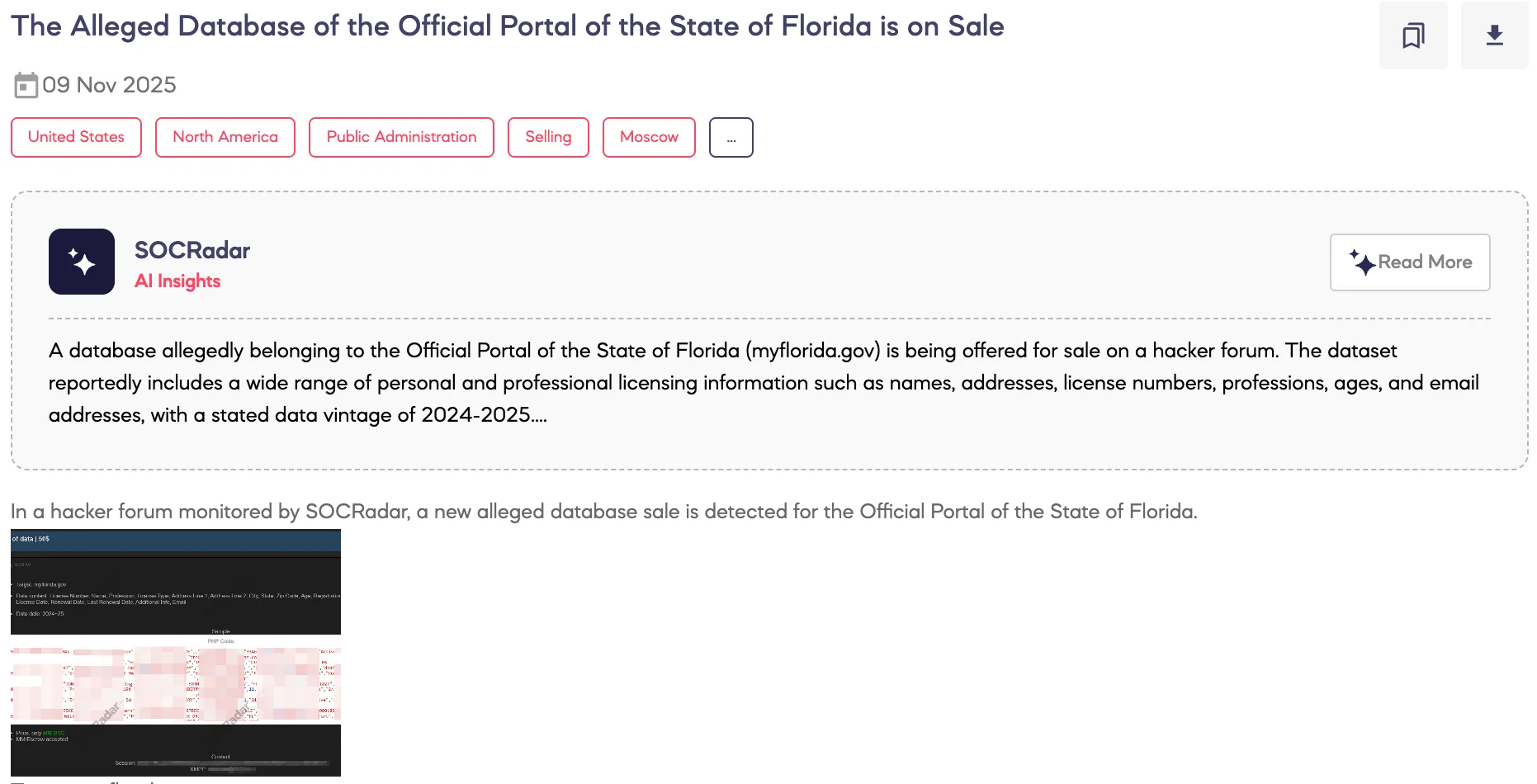
SOCRadar Dark Web Team detected on a hacker forum that a threat actor advertised an alleged database belonging to the official portal of the State of Florida. The post claims the dataset targets myflorida[.]gov and contains license numbers, names, professions, license types, full addresses, city, state, zip code, age, registration numbers, status details, initial and renewal dates, additional information, and email addresses. The threat actor claims the data dates from 2024 to 2025 and includes a sample allegedly provided as proof of authenticity.
Alleged Unauthorized FTP Server Access Sale is Detected for an American Company
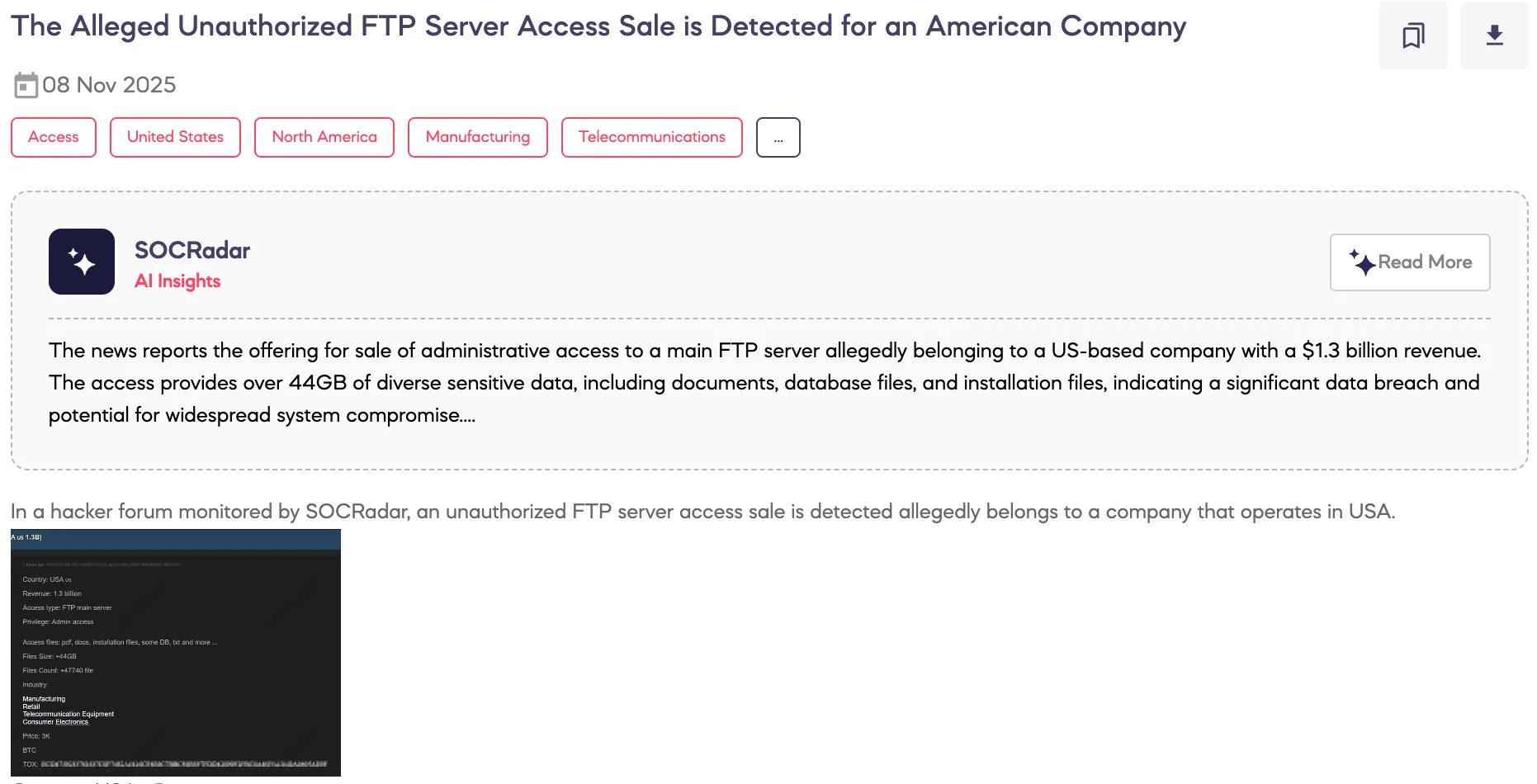
SOCRadar Dark Web Team detected on a hacker forum that a threat actor advertised alleged unauthorized FTP server access belonging to a company operating in the United States.
The post claims the access provides administrative privileges to the main FTP server and includes files such as PDFs, documents, installation files, databases, and text files, totaling over 44 GB and approximately 47,740 items. The threat actor claims the target company operates in the manufacturing, retail, telecommunication equipment, and consumer electronics sectors, reporting annual revenue of around 1.3 billion USD. The access is allegedly offered for sale at 3,000 USD in Bitcoin, with the actor providing a TOX contact for negotiation.
Alleged Database of Massachusetts Prisoners’ Legal Services Organization is on Sale
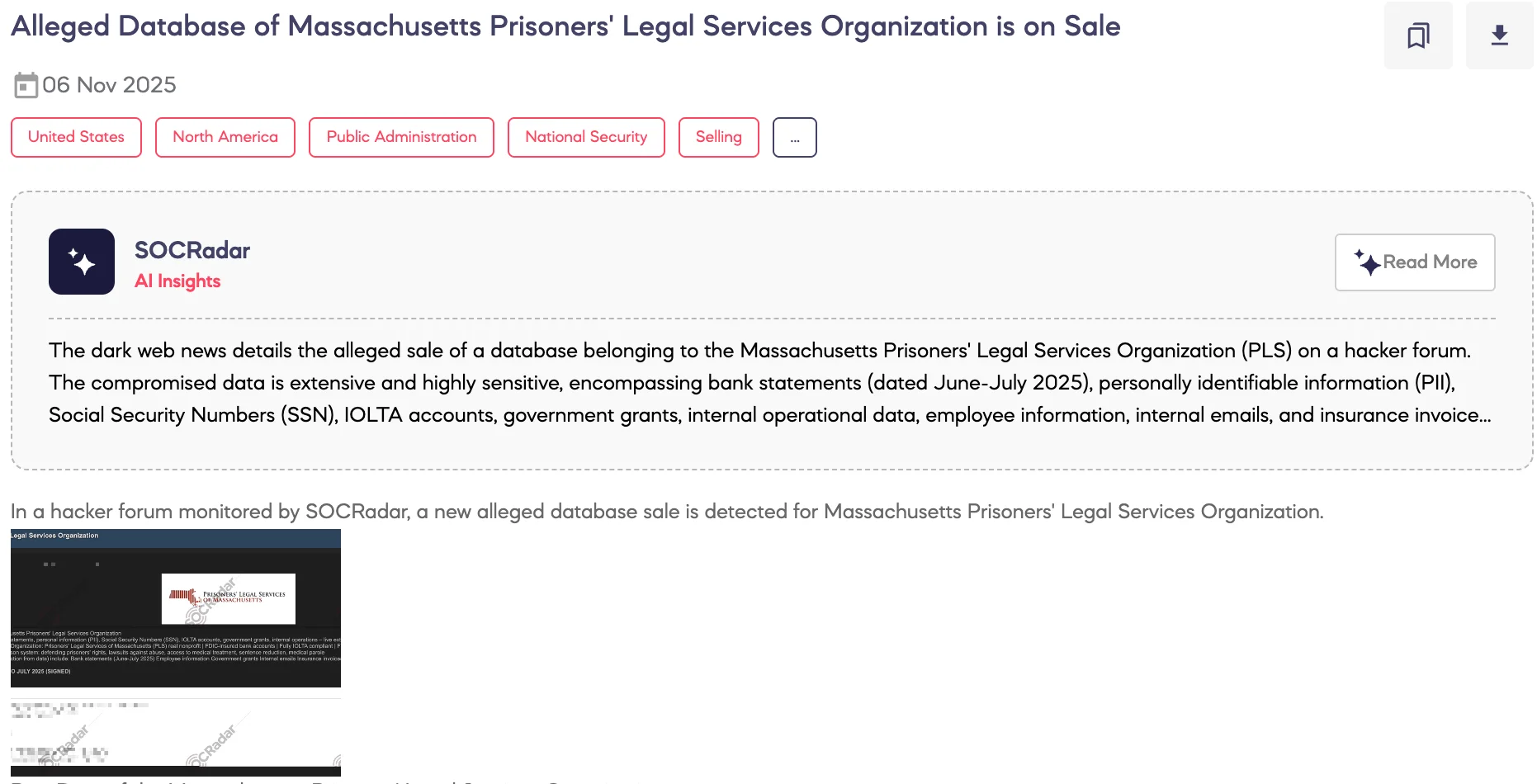
SOCRadar Dark Web Team detected on a hacker forum that a threat actor advertised an alleged database sale for the Prisoners’ Legal Services of Massachusetts (PLS).
The post claims the dataset is a raw extraction from PLSMA[.]org and includes bank statements, personal identifying information (PII) including Social Security numbers, IOLTA account details, government grant records, internal operation documents, and other sensitive files. The threat actor claims the extraction occurred in November 2025 and lists key samples such as bank statements (June–July 2025), employee records, government grant files, internal emails, insurance invoices (BCBS), HRA funding records, and payroll data.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.
Article Link: https://socradar.io/florida-government-data-binance-checker-and-legal-organization-leak-surface-on-dark-web/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics

