Rolladen Planet Data Sale, Windows 0-Day, and New macOS RAT Detected
Rolladen Planet Data Sale, Windows 0-Day, and New macOS RAT Detected
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
SOCRadar’s Dark Web Team identified several new underground listings this week, including an alleged customer database sale linked to German retailer Rolladen Planet, new malware tools targeting Windows and macOS systems, and a stealer service marketed as Flex Stealer. Additional posts advertised a zero-day Windows Local Privilege Escalation exploit and a modular macOS Remote Access Trojan. All details are based on threat actor claims and remain unverified at this stage.
Receive a Free Dark Web Report for Your Organization:
The Alleged Database of Rolladen & Rolltore is on Sale

The SOCRadar Dark Web Team has detected a new data leak claim targeting Rolladen Planet, a German e-commerce retailer specializing in roller shutters, gates, and sun protection systems. The company is described as an established player with over two decades of experience in the European market, serving a substantial customer base across Germany and Austria.
A threat actor has listed a database for sale on a cybercrime forum, purportedly containing detailed customer records. The dataset is being offered for $600, with the seller accepting escrow services to facilitate the transaction. Based on the sample data provided, the leak appears to encompass extensive Personally Identifiable Information (PII) and business-related data, including:
- Personal Details: Full names, salutations, and gender.
- Contact Information: Email addresses, phone numbers, and fax numbers.
- Physical Locations: Full billing/shipping addresses (Street, Number, Zip Code, City, State).
- Business Identifiers: Company names, department details, and VAT IDs (ustid).
- Account Metadata: User IDs and internal customer numbers.
New Flex Stealer Tool Sale is Detected
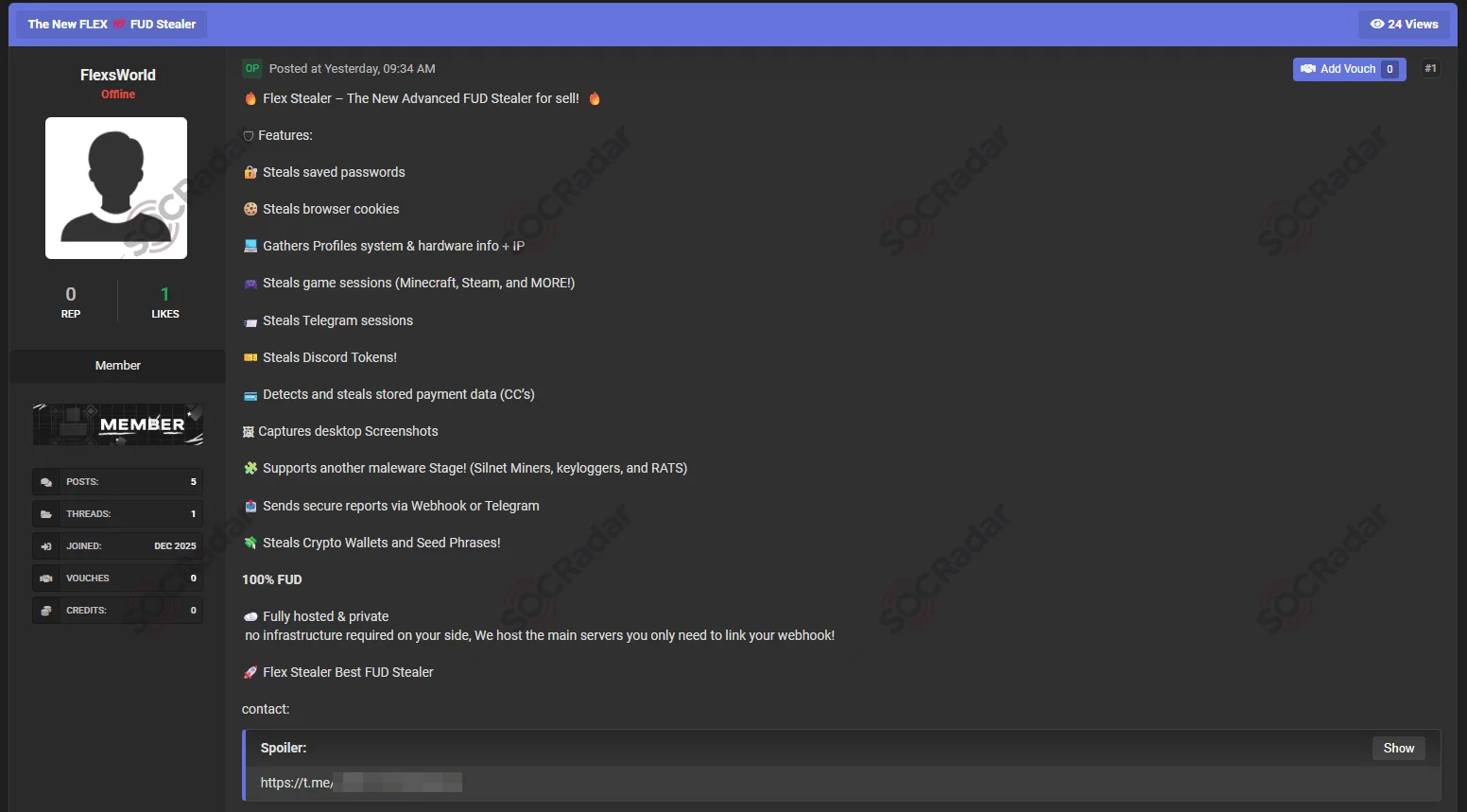
The SOCRadar Dark Web Team has identified a new listing for a malicious software tool named Flex Stealer. The threat actors advertise this malware as a stealthy solution capable of evading standard antivirus detection. It is provided as a fully managed service, which removes the requirement for buyers to establish their own server infrastructure. Operators simply need to connect a Webhook to receive the stolen information.
The malware is designed to harvest a wide range of sensitive data. This includes browser-stored assets such as passwords, cookies, and payment card numbers. The tool also specifically targets gaming platforms like Steam and Minecraft, as well as session tokens from communication applications such as Discord and Telegram. Additionally, the software seeks to identify and exfiltrate cryptocurrency wallets and recovery phrases.
Significantly, Flex Stealer supports the deployment of secondary malicious payloads. The threat actors assert that the tool can function as a delivery mechanism for silent cryptocurrency miners, keyloggers, or Remote Access Trojans, allowing for expanded exploitation of the infected system.
The Alleged 0-Day LPE Exploit of Microsoft Windows is on Sale
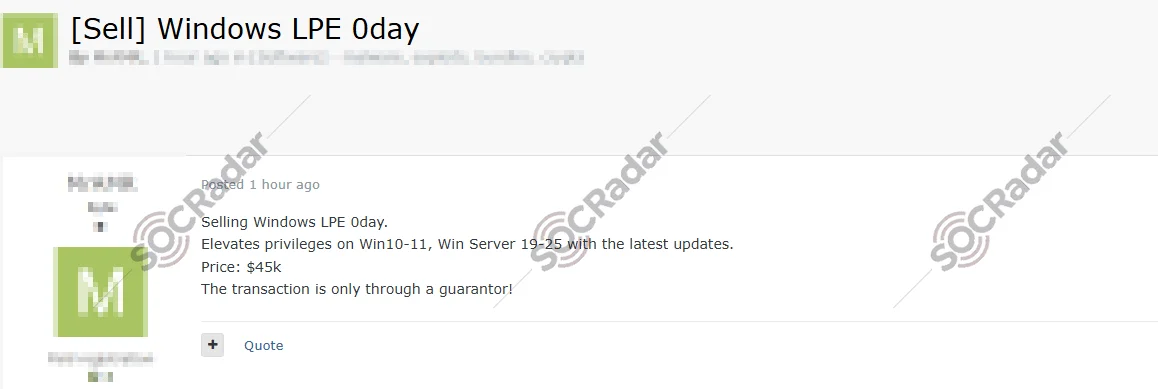
The SOCRadar Dark Web Team has detected a critical new listing on an underground forum where a threat actor is offering a Zero-Day (0-Day) exploit targeting the Microsoft Windows operating system. The seller claims that this exploit facilitates Local Privilege Escalation (LPE), allowing an unauthorized user to gain elevated administrative rights on a compromised machine.
According to the threat actor, the exploit is effective against the latest versions of the operating system, including Windows 10 and Windows 11, as well as Windows Server 2019 through the upcoming Windows Server 2025. The seller asserts that the code functions correctly even on systems with the most recent security updates installed. The listing price is set at $45,000, and the actor explicitly requires the use of a forum guarantor (escrow service) to finalize the transaction
Alleged A New RAT Malware for macOS is on sale
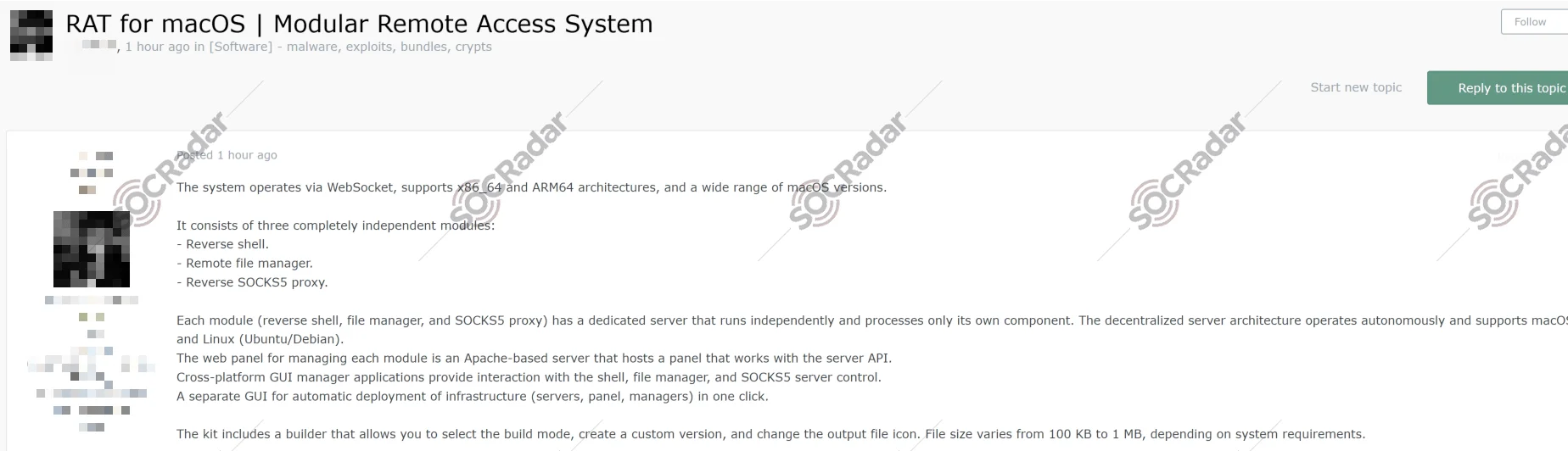
The SOCRadar Dark Web Team has detected a new listing on a cybercrime forum offering a sophisticated Remote Access Trojan (RAT) designed specifically for macOS. The threat actor describes the malware as a modular system that operates via WebSocket and supports both x86_64 (Intel) and ARM64 (Apple Silicon/M1/M2/M3) architectures, ensuring compatibility with a wide range of macOS versions.
The malware is structured around three completely independent modules: a Reverse Shell for command execution, a Remote File Manager for data theft or manipulation, and a Reverse SOCKS5 Proxy to route network traffic. The actor highlights a decentralized infrastructure where each module connects to its own dedicated server, which can run on macOS or Linux (Ubuntu/Debian). The kit includes a builder tool allowing buyers to customize the output file’s icon and build mode, with payload sizes ranging from 100 KB to 1 MB.
The pricing is set at $2,000 for the source code of a single module, or $5,000 for the complete set containing all three modules, the builder, the web panel, and the GUI manager. The seller also mentions that persistence features (save and launch) can be added for an extra fee.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.
Article Link: https://socradar.io/blog/rolladen-planet-windows-0-day-macos-rat-sale/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics

