Silent Push IDs More Than 10,000 Infected IPs as Part of SystemBC Botnet Malware Family
Key Findings
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
- Using a custom-built SystemBC tracker, Silent Push Preemptive Cyber Defense Analysts identified more than 10,000 unique infected IP addresses as part of this botnet—some of which were later linked to ransomware activity dating back to 2019.
- Our analysis shows SystemBC infections are globally distributed at scale, with the highest concentration of infected IP addresses observed in the United States, followed by Germany, France, Singapore, and India.
- We identified SystemBC infections within sensitive infrastructure, including compromised IP addresses hosting government websites in Burkina Faso and Vietnam.
- SystemBC command-and-control (C2) infrastructure has been observed leveraging abuse-tolerant bulletproof hosting, including BTHoster (bthoster[.]com) and AS213790 (BTCloud).
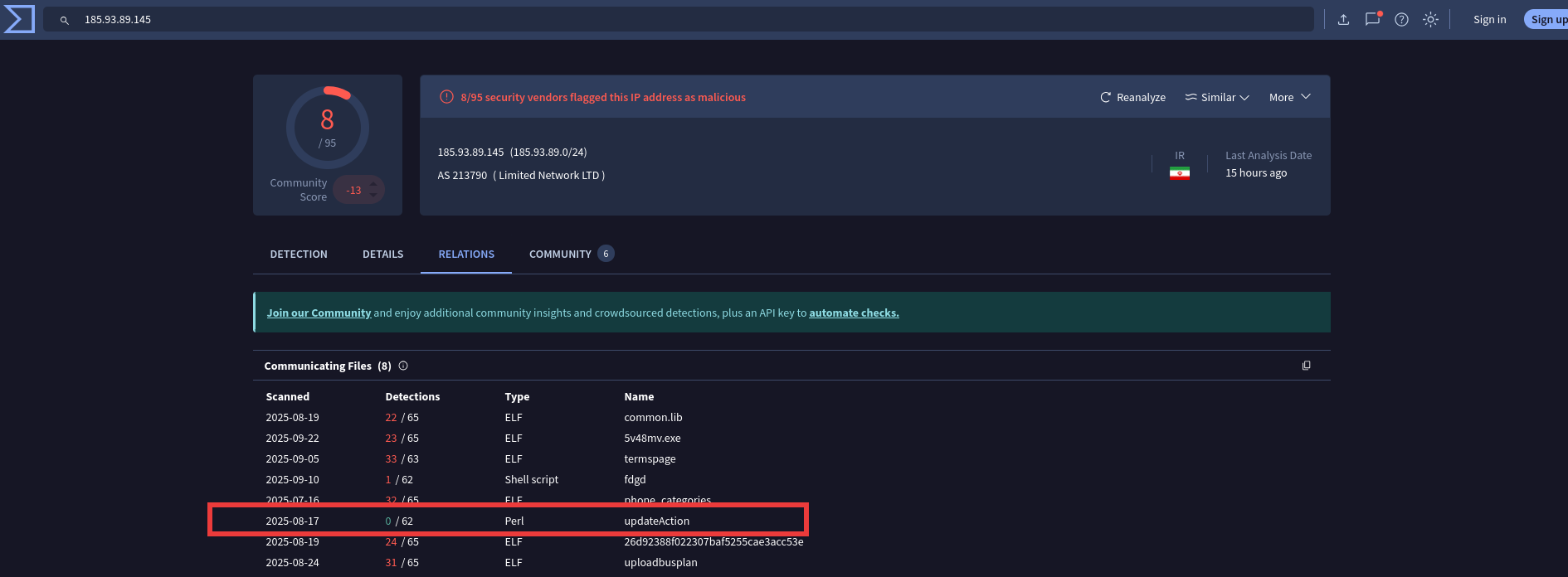
- Our research uncovered a previously undocumented SystemBC variant written in Perl, indicating continued development activity and ongoing evolution of the malware family.
Executive Summary
First documented publicly in 2019, SystemBC (also known as “Coroxy” or “DroxiDat”) is a long-running, multi-platform proxy malware that converts compromised systems into SOCKS5 proxies—and, in some cases, deploys additional malware.
Serving two primary functions, SystemBC proxies traffic through compromised systems and acts as a backdoor to maintain external access to infected internal networks. Some variants, including the Windows version, have been observed dropping additional malware, often alongside ransomware payloads, to tunnel malicious traffic back to attacker-controlled C2 infrastructure. The result is a resilient, anonymizing design that expands the potential blast radius of a compromise.
In May 2024, SystemBC was among the malware families targeted during Europol’s Operation Endgame, a coordinated effort to disrupt large-scale criminal infrastructure. That attention mirrors years of public reporting linking SystemBC activity to breaches that culminated in ransomware deployment—reinforcing why early detection of this activity matters.
Silent Push began tracking SystemBC in 2025, quickly identifying its recurring role in intrusion campaigns that precede ransomware deployment. This led to the development of a SystemBC-specific tracking fingerprint to expand visibility into active infections and supporting infrastructure. Using that fingerprint, our team identified more than 10,000 unique infected IP addresses worldwide, with infrastructure tied to ransomware activity dating back to 2019. Across the dataset, infections were widespread: the largest concentrations of detected victims appeared in the U.S., followed by Germany, France, Singapore, and India.
The dataset also captured infections in sensitive government environments, such as compromised high-density IP addresses hosting official websites in Burkina Faso and Vietnam. That same analysis revealed a previously undocumented SystemBC variant written in Perl, underscoring that this malware is continuing to evolve.
Table of contents
Background
SystemBC is a multi-platform proxy malware that turns infected systems into SOCKS5 proxies, allowing all kinds of malicious traffic to be sent through them. Also known as “Coroxy” or “DroxiDat,” SystemBC was first documented by Proofpoint in 2019. Upon reviewing several forum posts by the creator, written in Russian, our team believes the creator may be Russian or have ties to the country.
SystemBC is commonly used to proxy traffic through compromised systems or to maintain persistent access to internal networks. In some cases, including observed Windows variants, SystemBC has also been used to deploy additional malware, meaning its presence may indicate broader compromise or follow-on infections on the affected system. When a victim server is compromised, SystemBC uses a custom binary protocol and RC4 encryption to encapsulate SOCKS5 traffic.
Unlike virtual private networks (VPNs), SOCKS/SOCKS5 is a specific internet protocol for proxies. Proxies are versatile network protocols that act as middlemen, or relays, between devices and the internet. They can route internet traffic (TCP, UDP, etc.) for different applications, masking IP addresses to bypass online blocks, access geo-restricted content, and enhance privacy for specific applications. Many threat actors use proxies to hide their real infrastructure from defenders.
Since most infected systems are not directly reachable over the internet, SystemBC employs a “backconnect,” or rotating, architecture: clients connect to the exposed C2 servers, which then relay traffic through the infected systems, acting as proxies. This design enables threat actors to route external traffic through compromised hosts and expose otherwise internal networks to external access, thereby significantly increasing the potential impact of any compromise.
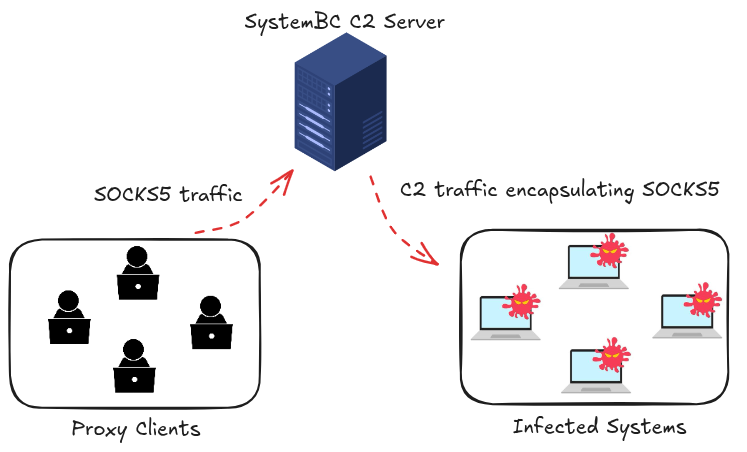 Simple map of SystemBC’s network traffic
Simple map of SystemBC’s network trafficInitial Intelligence
Investigations have repeatedly documented SystemBC’s role in intrusions that later escalate into ransomware deployment. SystemBC was targeted during Europol’s Operation Endgame in May 2024, but updates from its developer, “psevdo,” continue to appear on the Russian-language forum forum[.]exploit[.]in. This activity prompted deeper analysis—uncovering a highly active SystemBC C2 cluster, a previously undocumented Perl variant, and a trail of global victims.
Psevdo’s updates are written in Russian, with selected translations shown below:
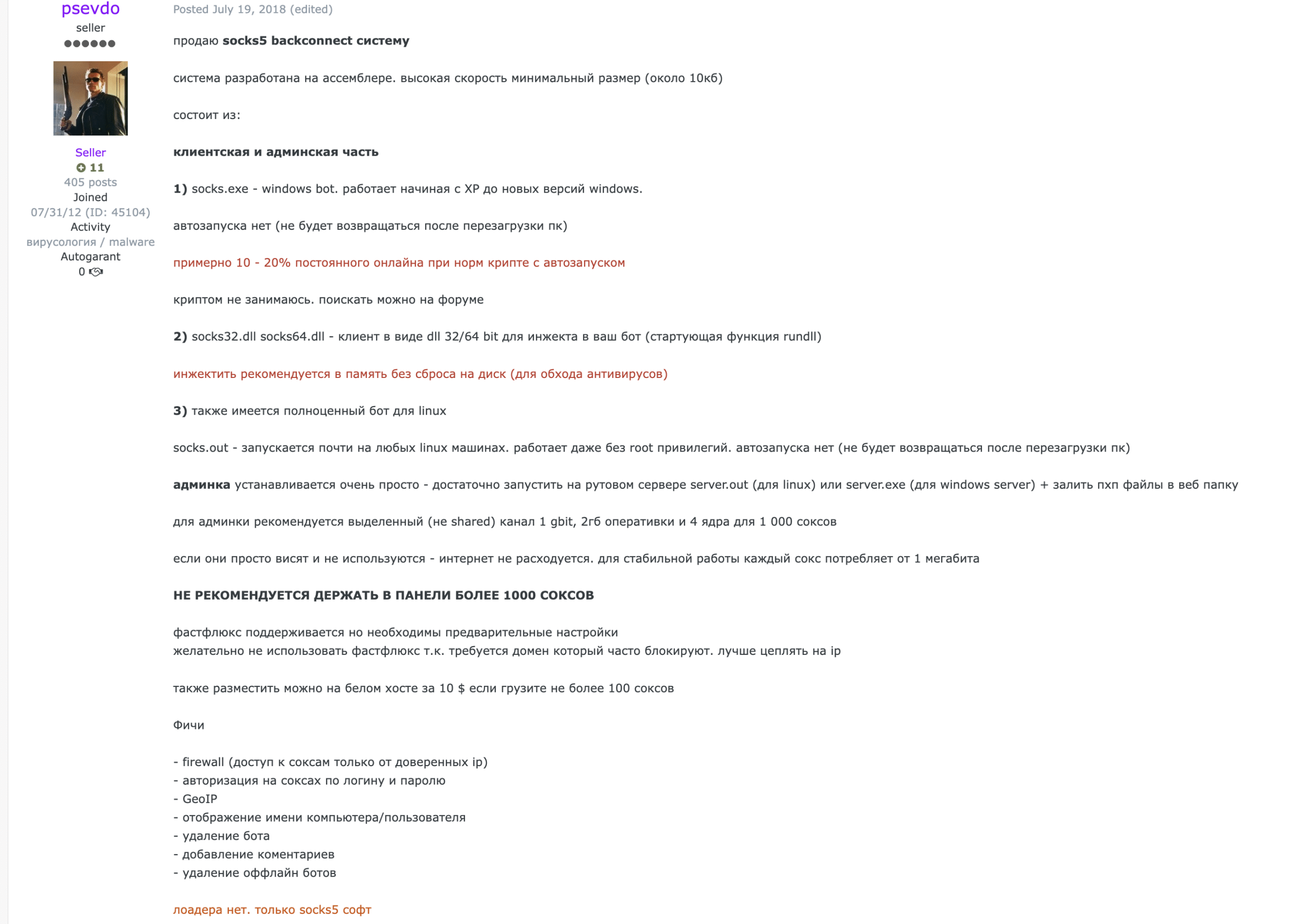 Screenshot of psevdo’s announcements (in Russian), posted on July 19, 2018
Screenshot of psevdo’s announcements (in Russian), posted on July 19, 2018Post-Endgame forum activity shows the codebase continuing to evolve:
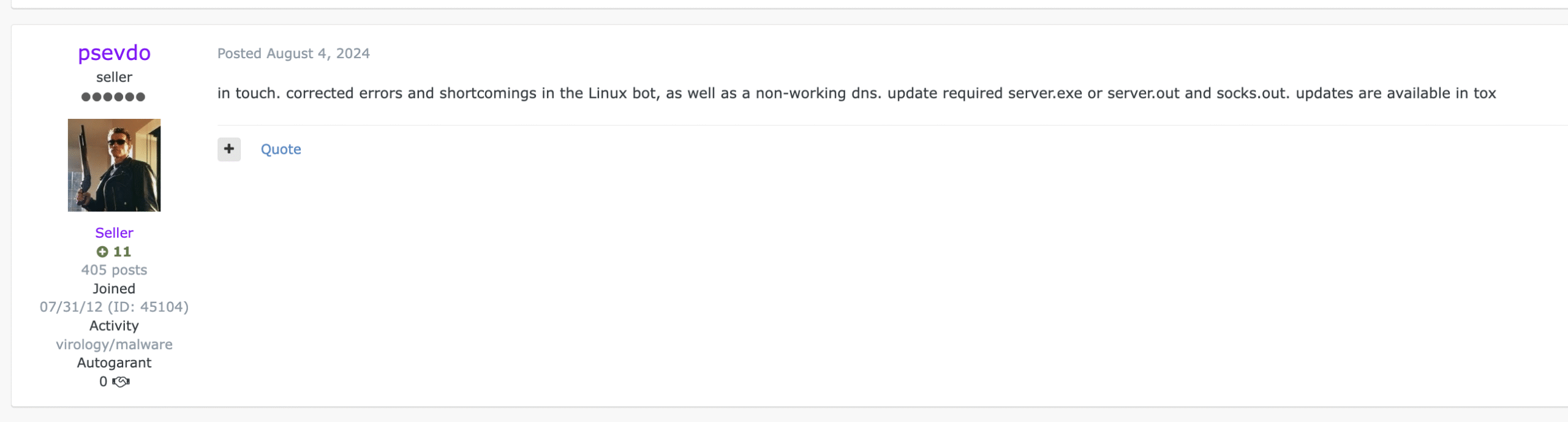 Announcement of “Linux bot and C2 server updates”
Announcement of “Linux bot and C2 server updates”(Russian text translated to English)
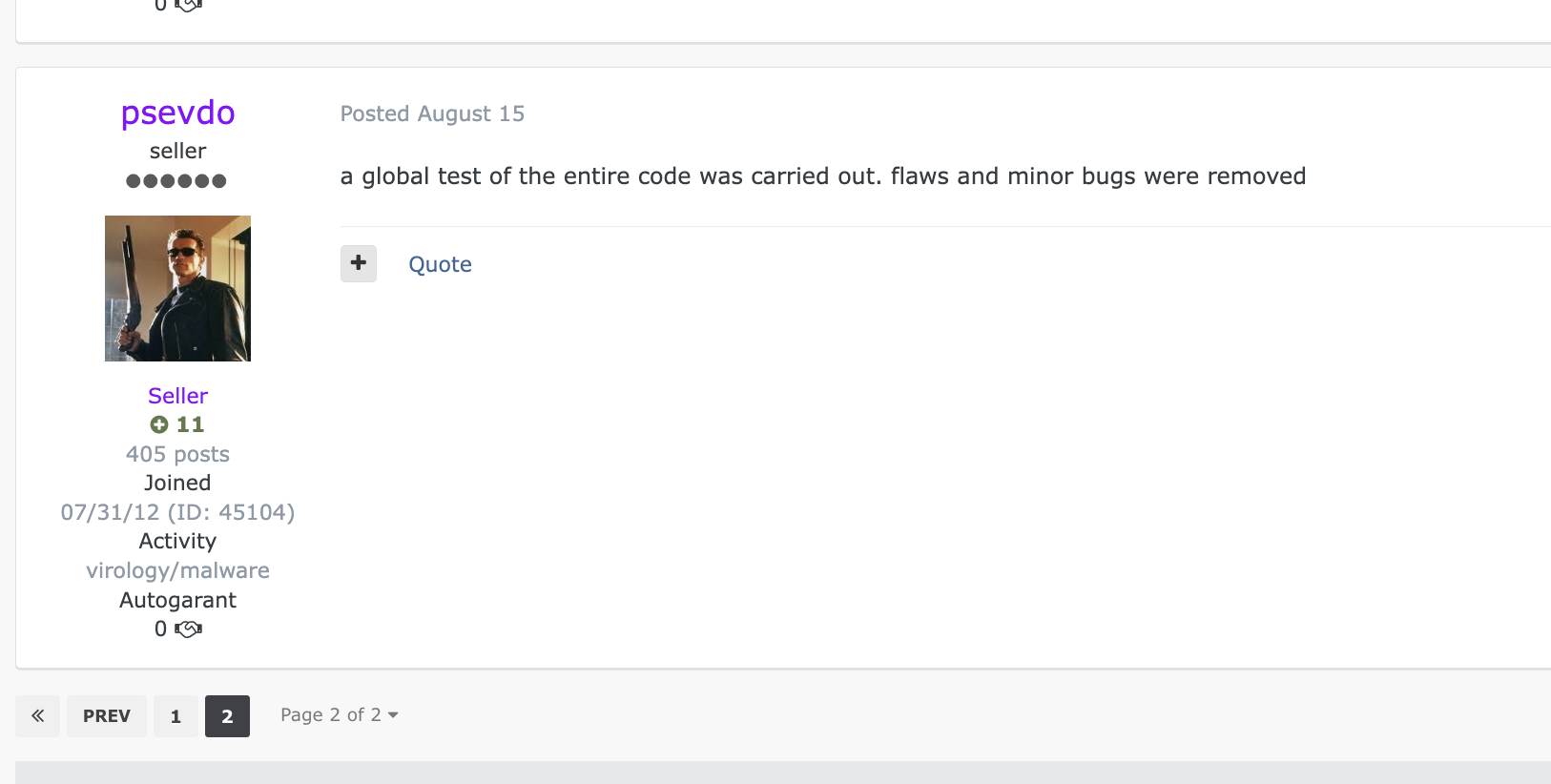 Announcement of “global tests and bug fixes”
Announcement of “global tests and bug fixes”(Russian text translated to English)
The continued forum activity suggests that Operation Endgame did not, in fact, mark the end of SystemBC development.
Same Threat, New Platform
Files we saw communicating with a known C2 in this cluster included an unusual Perl script, which had zero detections across the 62 antivirus engines on VirusTotal.
Further analysis revealed the Perl script was a previously undocumented SystemBC variant designed specifically to infect Linux systems.
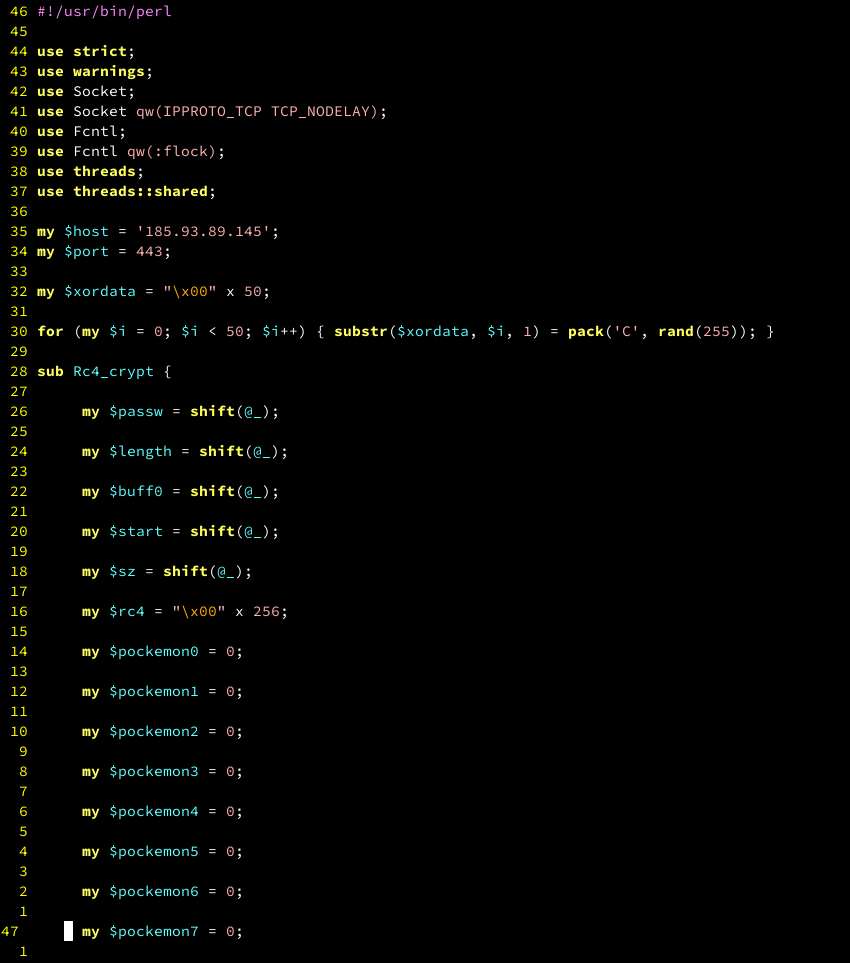 Example of the SystemBC Perl variant
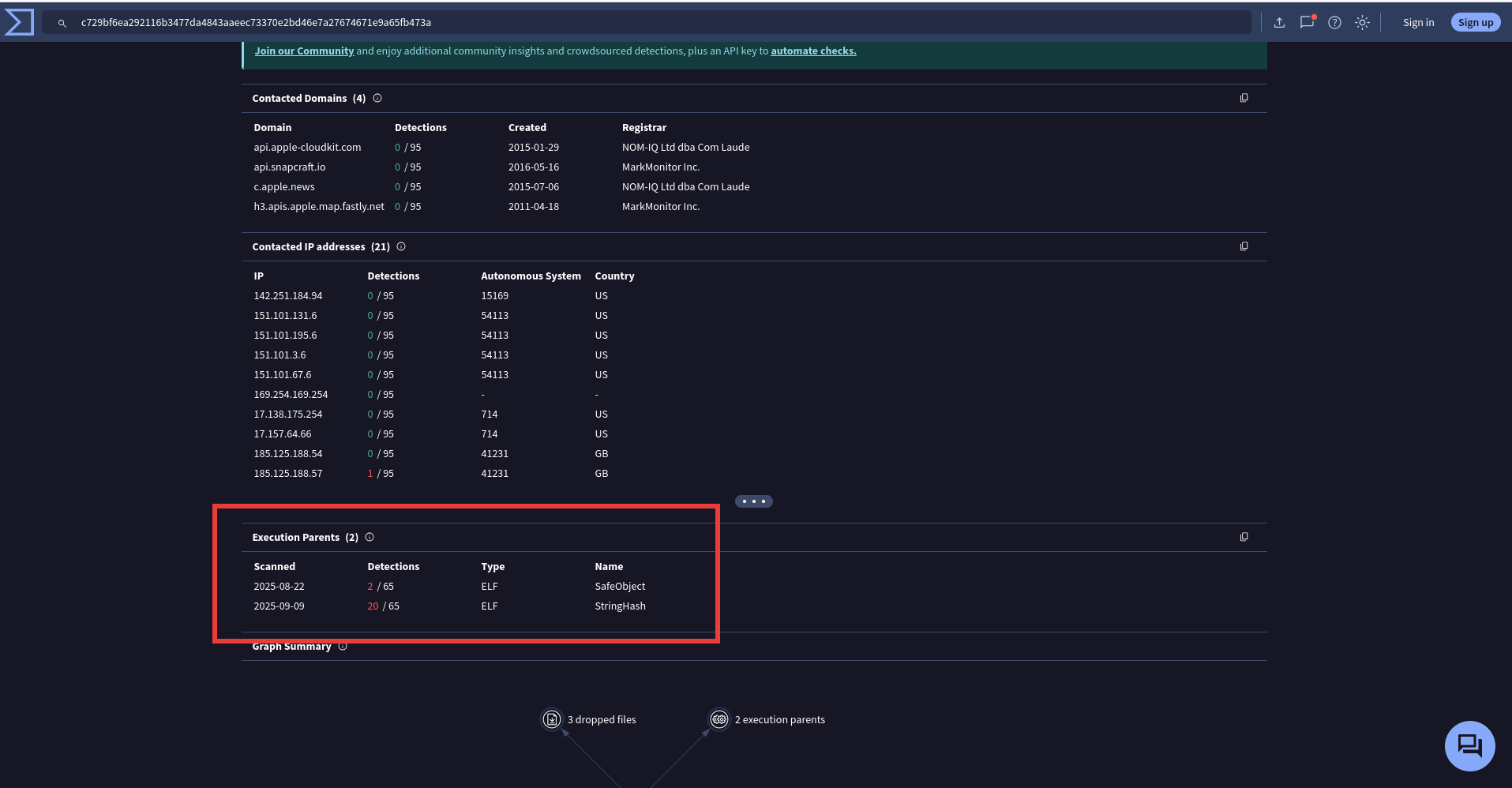
Example of the SystemBC Perl variantExamining the files that dropped the Perl script revealed two additional ELF binaries: SafeObject and StringHash.
The SafeObject file is a UPX-packed variant of StringHash. Once unpacked, it recursively hunts for writable directories before dropping and executing 264 embedded SystemBC payloads, including both ELF and Perl variants.
Behavior aside, the dropper is unusually noisy and littered with Russian-language strings—an unscientific but familiar clue about the threat actor’s origins.
 Screenshot of Russian strings observed
Screenshot of Russian strings observedWhere Infections Hit Hardest
Much of the SystemBC C2 infrastructure observed here appears to rely on hosting tied to abuse-tolerant providers, including BTHoster-linked environments and AS213790 (BTCloud). Zeroing in on the AS213790-hosted cluster alone, we identified more than 10,340 distinct victim IP addresses. Activity was steady—averaging roughly 2,888 victim IPs per day—with infections persisting far longer than typical. On average, systems remained infected for 38 days, with some lasting more than 100 days.
The highest concentration of infected systems seen in our analysis was in the U.S., with more than 4,300 affected IPs. Germany (829), France (448), Singapore (419), and India (294) followed.
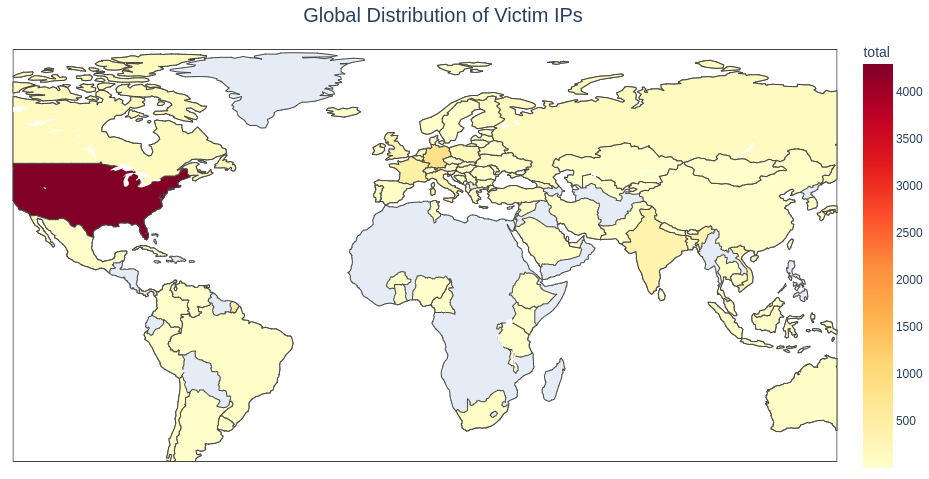 Global distribution of IP addresses map
Global distribution of IP addresses mapASNs Tied to Victim IP Addresses
Looking at the ASNs tied to victim IPs, this cluster overwhelmingly targets hosting providers rather than residential networks, which helps explain why infections tend to linger—residential IPs typically change far more frequently.
| ASN | AS Name | AS Type |
|---|---|---|
| 19871 | NETWORK-SOLUTIONS-HOSTING | Hosting |
| 46606 | UNIFIEDLAYER-AS-1 | Hosting |
| 22612 | NAMECHEAP-NET | Hosting |
| 398101 | GO-DADDY-COM-LLC | Hosting |
| 8560 | IONOS-AS | Hosting |
| 16509 | AMAZON-02 | Hosting |
| 16276 | OVH | Hosting |
| 24940 | HETZNER-AS | Hosting |
| 26496 | AS-26496-GO-DADDY-COM-LLC | Hosting |
| 14061 | DIGITALOCEAN-ASN | Hosting |
Table of the top 10 ASNs tied to victim IP addresses
Reviewing PADNS data led to an unexpected finding: infections tied to multiple government domains. One example surfaced at IP address 103.28.36[.]105, a sizable cloud host that was also found hosting phutho.duchop[.]gov[.]vn, a Vietnamese provincial government website.
![Silent Push Total View of IP address 103.28.36[.]105](https://www.silentpush.com/wp-content/uploads/sysbc-image-10-total-view-screenshot.png) Silent Push Total View of IP address 103.28.36[.]105
Silent Push Total View of IP address 103.28.36[.]105![Silent Push Total View of domain phutho.duchop[.]gov[.]vn](https://www.silentpush.com/wp-content/uploads/sysbc-image-11-phuto-total-view.png) Silent Push Total View of domain phutho.duchop[.]gov[.]vn
Silent Push Total View of domain phutho.duchop[.]gov[.]vn![Screenshot of phutho.duchop[.]gov[.]vn website](https://www.silentpush.com/wp-content/uploads/sysbc-image-12-phuto-site.png) Screenshot of phutho.duchop[.]gov[.]vn website
Screenshot of phutho.duchop[.]gov[.]vn websiteIP address 196.13.207[.]92, meanwhile, was linked to domains associated with the Government of Burkina Faso in West Africa.
![Screenshot of IP address 196.13.207[.]92 revealing ties to the Burkina Faso government](https://www.silentpush.com/wp-content/uploads/sysbc-image-13-table-burkina-faso.png) Screenshot of IP address 196.13.207[.]92 revealing ties to the Burkina Faso government
Screenshot of IP address 196.13.207[.]92 revealing ties to the Burkina Faso government![Screenshot of concours[.]gov[.]bf website](https://www.silentpush.com/wp-content/uploads/sysbc-image-14-concours-bf.png) Screenshot of concours[.]gov[.]bf website
Screenshot of concours[.]gov[.]bf websiteMany infected IP addresses have been reported in VirusTotal comments for engaging in WordPress exploitation activity. Taken together, these observations indicate that threat actors are using SystemBC-associated proxies to target WordPress websites.
![Screenshot of 202.142.184[.]234 on VirusTotal](https://www.silentpush.com/wp-content/uploads/sysbc-image-15-202-142-184-234.png) Screenshot of 202.142.184[.]234 on VirusTotal
Screenshot of 202.142.184[.]234 on VirusTotal![Screenshot of 148.113.208[.]227 on VirusTotal](https://www.silentpush.com/wp-content/uploads/sysbc-image-16-148-113-208-227.png) Screenshot of 148.113.208[.]227 on VirusTotal
Screenshot of 148.113.208[.]227 on VirusTotal![Screenshot of 103.112.211[.]167 on VirusTotal](https://www.silentpush.com/wp-content/uploads/sysbc-image-17-103-112-211-167.png) Screenshot of 103.112.211[.]167 on VirusTotal
Screenshot of 103.112.211[.]167 on VirusTotalInterested in Learning More About Preemptive Cyber Defense?
Our enterprise customers have access to the exclusive report we created for the SystemBC botnet family. If you would like to learn more about our capabilities for tracking adversarial frameworks—or how you can hunt for them on our platform—we encourage you/your organization to reach out to our team for a demonstration of Silent Push cyber defense technology.
Connect with our platform experts for an overview of the Silent Push Enterprise Edition platform. We are happy to provide you with a tailored walkthrough for your specific use case, along with insights into integrations and API capabilities.
Mitigation
SystemBC-associated infrastructure presents a sustained risk due to its role early in intrusion chains and its use across multiple threat actors. Proactive monitoring is critical, as activity tied to SystemBC is often a precursor to ransomware deployment and other follow-on abuse.
Our analysts have developed SystemBC-specific Indicators of Future Attack (IOFA
(IOFA ) feeds to help identify related infrastructure and emerging variants before they cause downstream impact. These feeds include:
) feeds to help identify related infrastructure and emerging variants before they cause downstream impact. These feeds include:
- SystemBC C2 Domains
- SystemBC C2 IPs
- SystemBC Infected IPs
The IOFA feeds are available as part of a Silent Push Enterprise subscription. Enterprise users can ingest this data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
feeds are available as part of a Silent Push Enterprise subscription. Enterprise users can ingest this data into their security stack to inform their detection protocols or use it to pivot across attacker infrastructure using the Silent Push Console and Feed Analytics screen.
SystemBC IPs
- 36.255.98[.]159
- 62.60.131[.]191
- 36.255.98[.]179
- 62.60.131[.]184
- 36.255.98[.]152
- 36.255.98[.]160
- 62.60.131[.]187
- 62.60.131[.]204
- 62.60.131[.]180
- 36.255.98[.]165
Malicious SystemBC SHA256 Hashes
SystemBC Perl
- c729bf6ea292116b3477da4843aaeec73370e2bd46e7a27674671e9a65fb473a
SystemBC Perl Droppers
- 0f5c81eaf35755a52e670c89b9546e7047828d83f346e3c29be1f6958e14a384
- da95384032f84228ef62f982f3c0f9e574dc6b06b606db33889ea6a5f93d6ae2
Ready to dive deeper into the world of preemptive cyber defense? Take our technology for a test drive with the free Silent Push Community Edition today.
Continuing to Track SystemBC
Our threat intelligence and research teams will continue to track the SystemBC malware while expanding our understanding of the code variants, victims, and methods for monitoring the associated infrastructure. We believe SystemBC remains an active threat to major enterprises and expect the Tactics, Techniques, and Procedures (TTPs) of the multiple threat actors leveraging this malware to continue evolving indefinitely.
If you or your organization has any information to share regarding the findings of this report, we would love to hear from you.
The post Silent Push IDs More Than 10,000 Infected IPs as Part of SystemBC Botnet Malware Family appeared first on Silent Push.
Article Link: Silent Push Identifies More Than 10,000 Infected IPs as Part of SystemBC Botnet Malware Family - Silent Push
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics