New Alleged Breaches: Bank Banten Customer Data, Deloitte Source Code, and TotalEnergies France
New Alleged Breaches: Bank Banten Customer Data, Deloitte Source Code, and TotalEnergies France
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Cybercriminal activity across the Dark Web continues to highlight the vulnerability of organizations and personal data. This week, SOCRadar’s Dark Web Team has tracked multiple high-profile incidents: two separate posts advertising Bank Banten’s customer and ATM data, an alleged source code leak tied to Deloitte’s U.S. consulting division, and the sale of a massive dataset allegedly linked to TotalEnergies France. Additional findings include a threat actor recruiting marketing partners for aggressive bulk messaging campaigns, reflecting the increasingly professionalized and targeted nature of underground cybercrime operations.
Receive a Free Dark Web Report for Your Organization:
Alleged Database of Bank Banten is on Sale
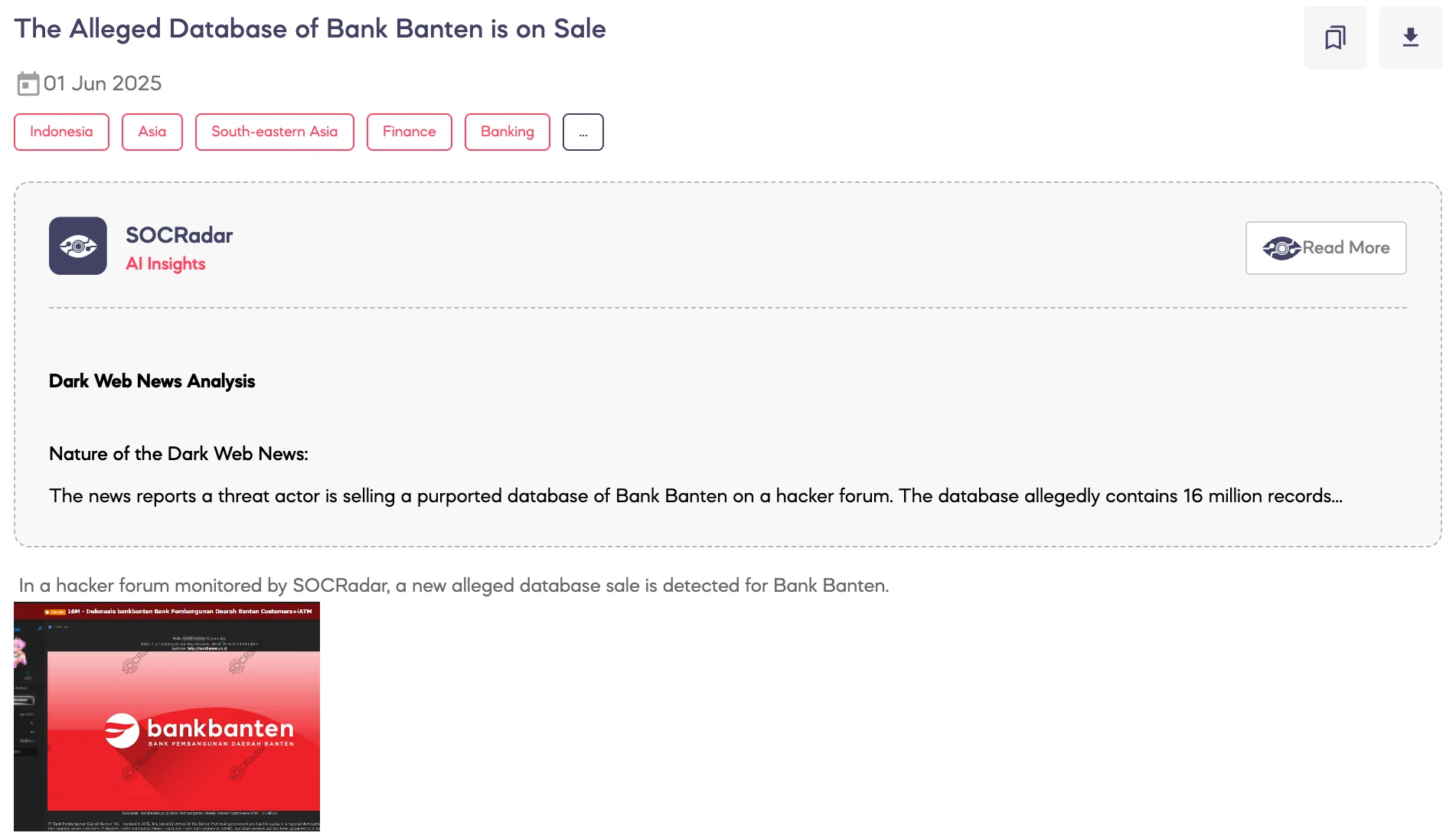
SOCRadar Dark Web Team has observed two separate posts on the same underground forum, both allegedly offering stolen data from Bank Banten, a regional development bank in Indonesia. The posts were shared by different threat actors on the same day.
In the first post, the threat actor claims to be selling a database containing approximately 16 million records linked to bankbanten.co.id. The dataset allegedly includes card details, individual data, user records, ATM card information, and internal banking logs (BPI and iATM).
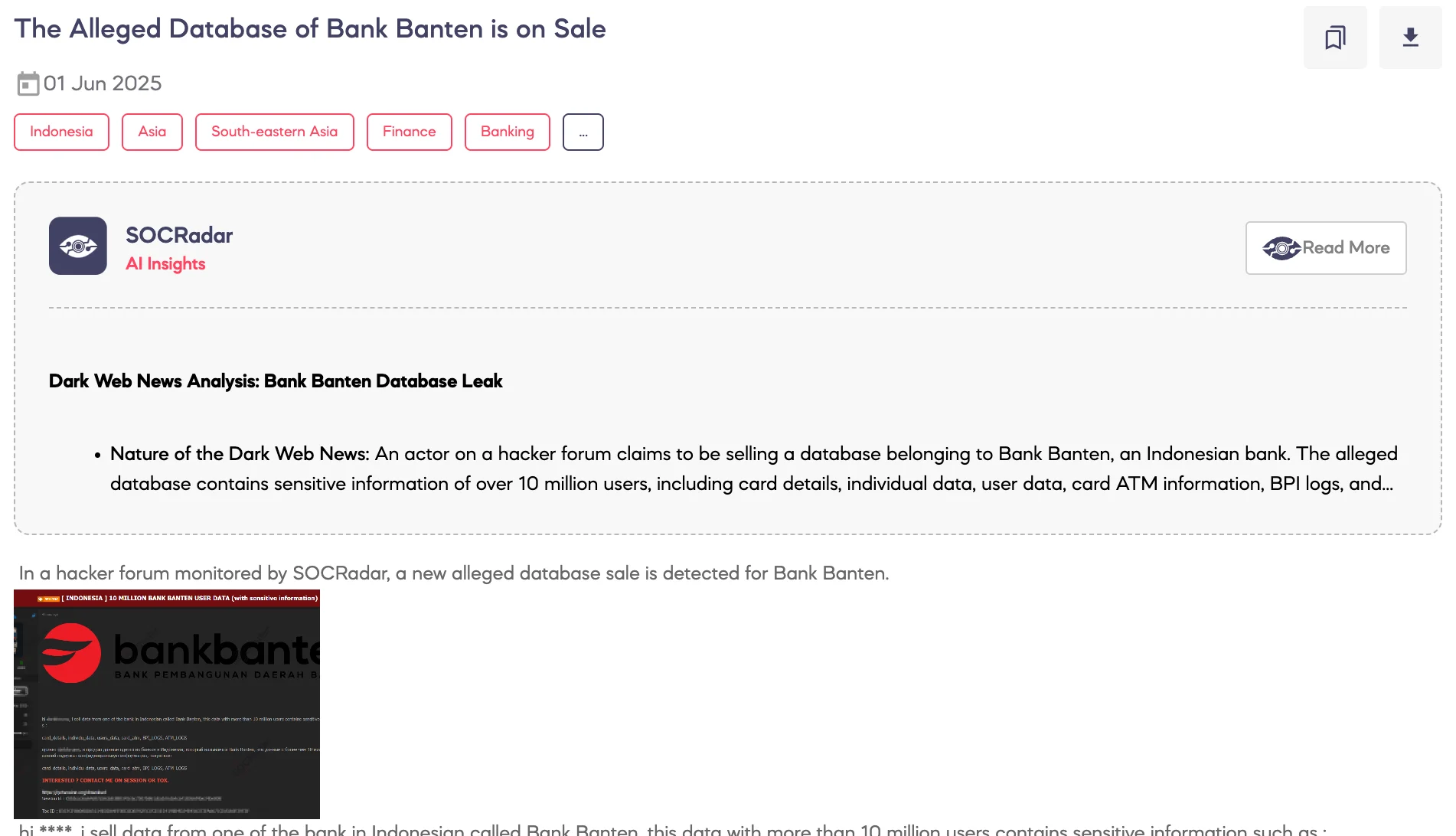
The second post, written in both English and Russian, also offers data allegedly sourced from Bank Banten. The vendor states the breach affects over 10 million users and contains sensitive details similar to those listed in the first post.
The nearly identical data types and timing raise several possibilities:
- Shared Source: Both actors may have obtained the data from the same initial breach or third-party supplier, and are now attempting to sell it independently to maximize profit or reputation.
- Re-upload by Same Actor Using Different Aliases: It’s possible that a single threat actor is using multiple identities to promote the same dataset, aiming to increase visibility or create a false sense of demand.
- Partial Access to the Same Dataset: Each actor might have acquired only parts of the full dataset, resulting in overlapping but not identical offerings.
- Different Stages of the Breach Lifecycle: One actor could be the original leaker, while the other is a reseller or aggregator who repackaged and reposted the information.
- Fabricated or Recycled Content: At least one of the posts might contain recycled or fabricated data, leveraging a real institution’s name to lure buyers without having genuine access.
Further validation, including analysis of shared samples and metadata, would be required to confirm the origin and authenticity of the data.
Alleged Source Code of Deloitte is Leaked
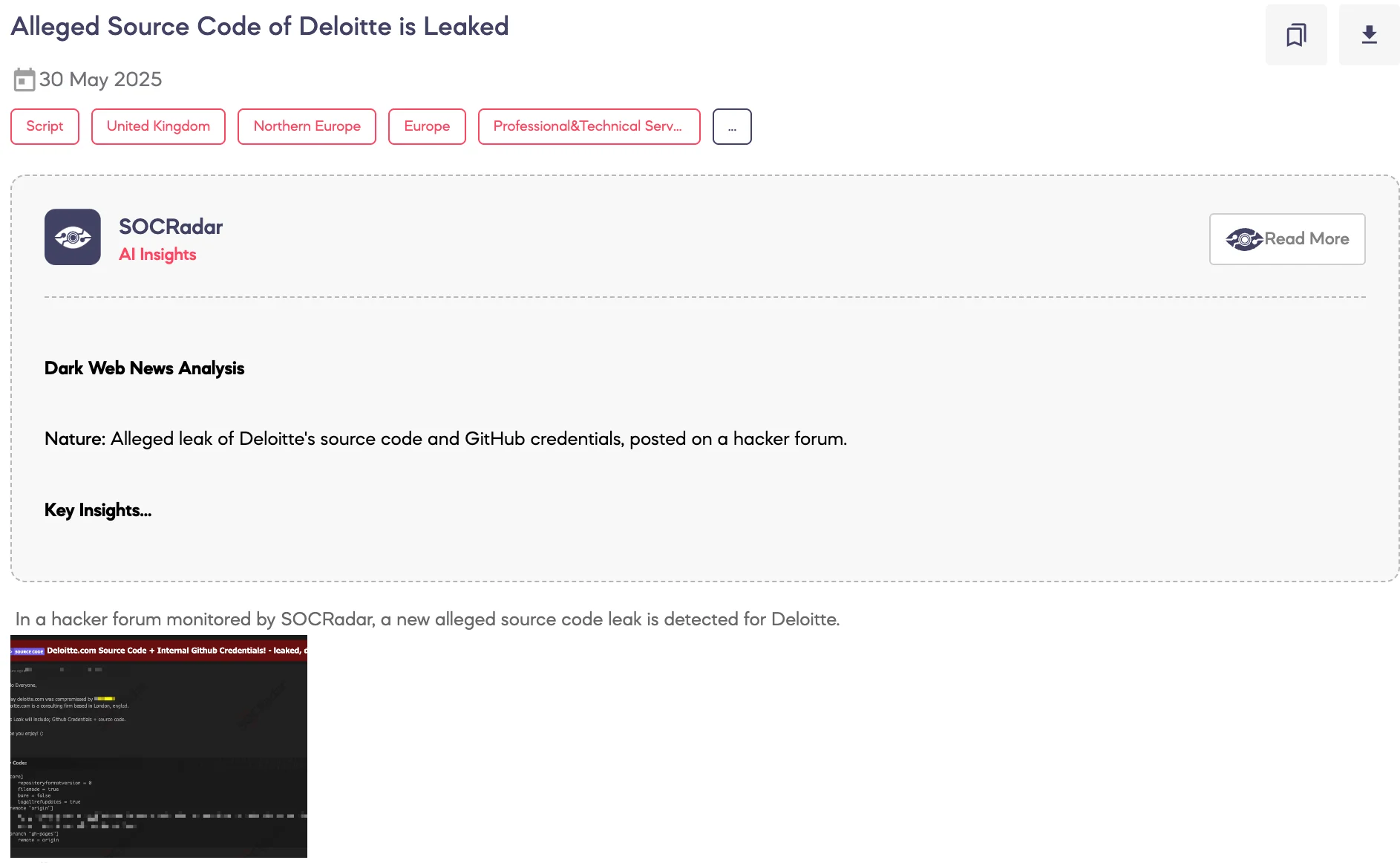
SOCRadar Dark Web Team has detected a dark web post allegedly exposing internal data from Deloitte.
The threat actor claims that Deloitte’s systems were compromised, leading to the leak of GitHub credentials and source code from internal project repositories tied to the company’s U.S. consulting division. If genuine, the exposed credentials could enable unauthorized access to Deloitte’s development infrastructure and proprietary software.
The alias used in the post matches that of a previously active member on BreachForums. However, BreachForums is currently offline, and it remains uncertain whether the post is linked to the same individual or simply a reused handle. The authenticity and impact of the leak have yet to be verified.
Alleged Data of TotalEnergies France are on Sale
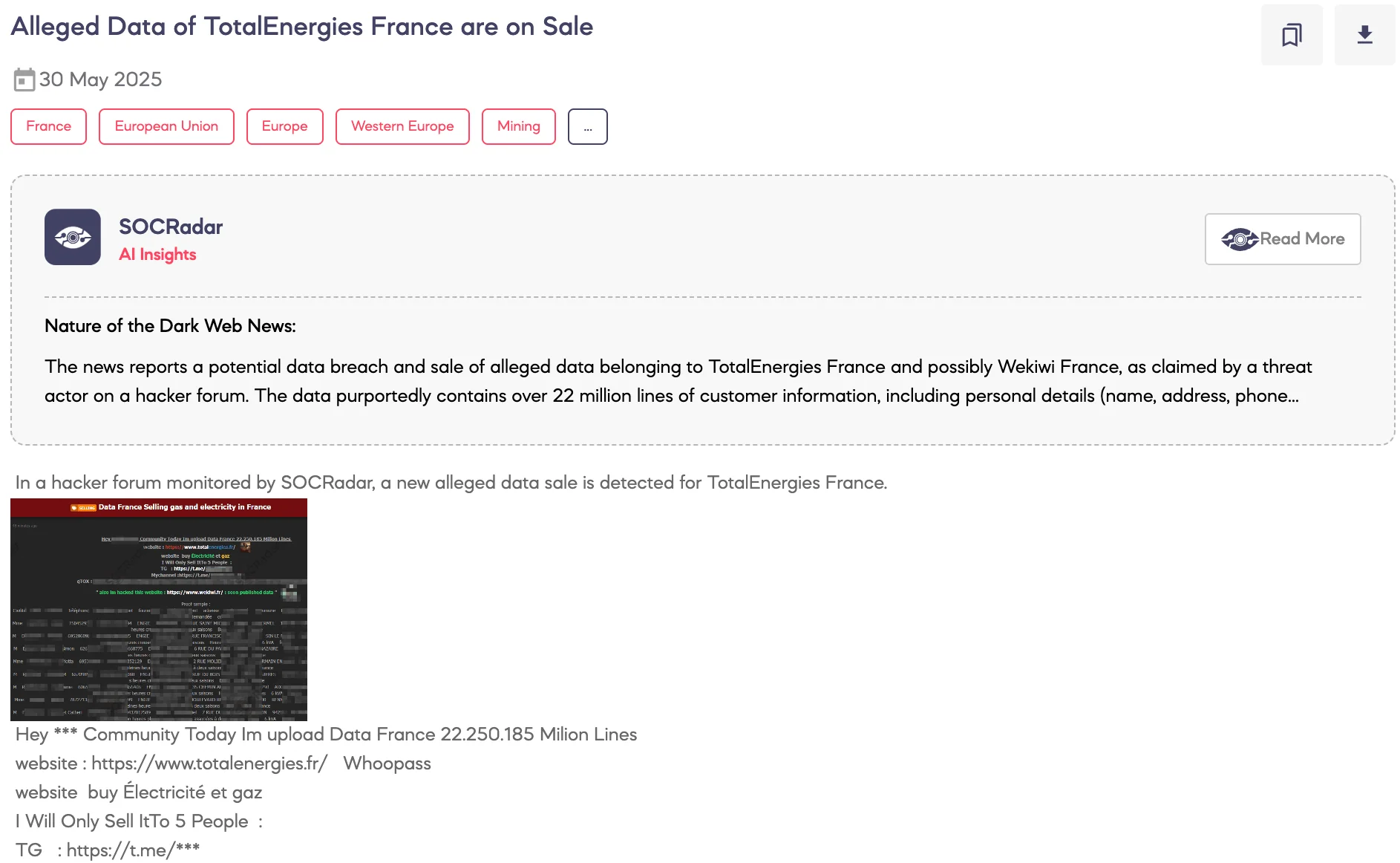
SOCRadar Dark Web Team has identified a post on a dark web forum offering a large dataset allegedly linked to TotalEnergies France.
The threat actor claims to hold over 22 million records tied to totalenergies.fr, including user data related to electricity and gas services. The dataset is advertised as exclusive and limited to five buyers, with contact provided via Telegram and qTox. The threat actor also claims to have breached another energy provider operating in France, Wekiwi, and states that its data will be published soon.
New Partnership Searching Post is Detected
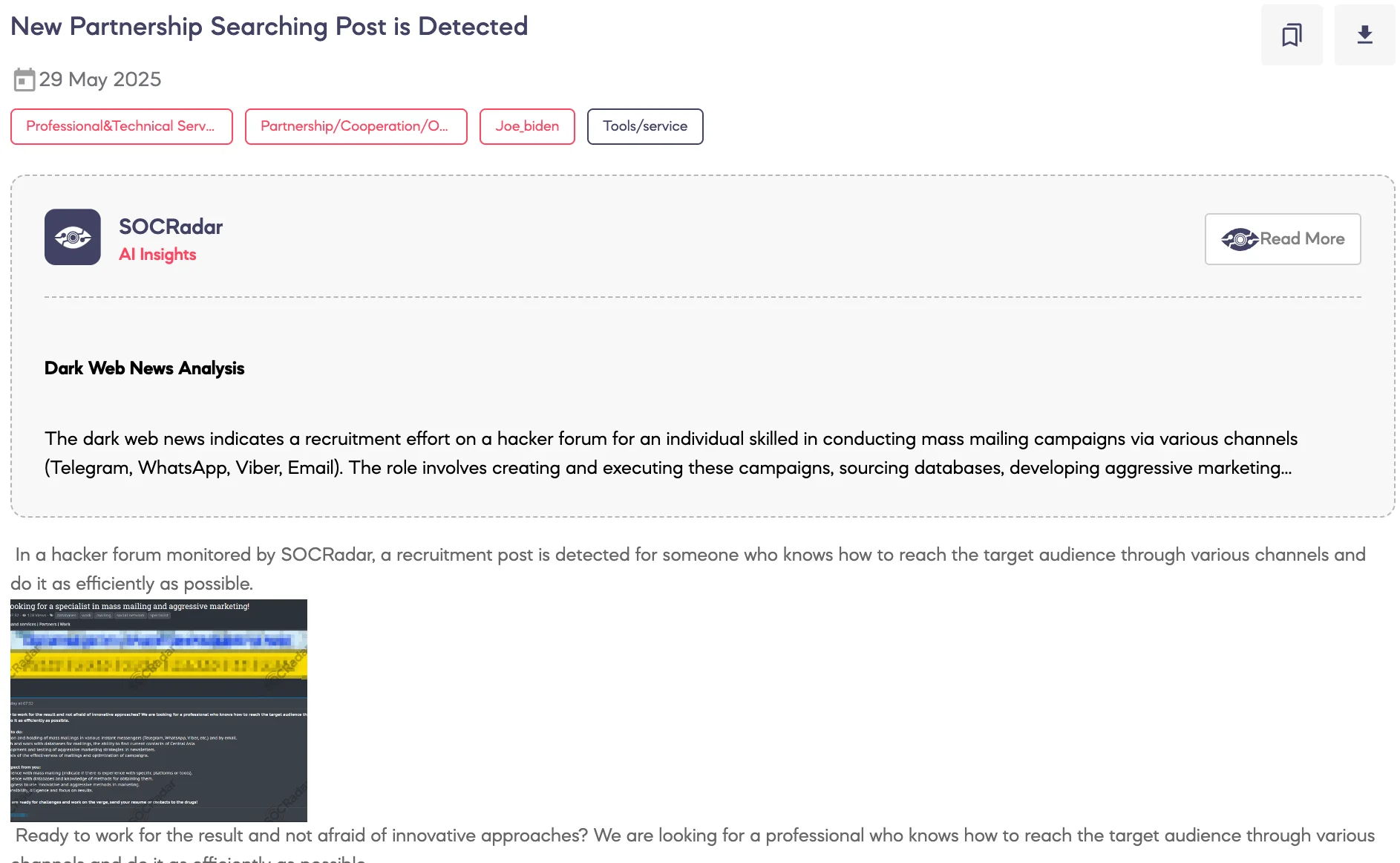
SOCRadar Dark Web Team has detected a recruitment post on a hacker forum seeking a partner with experience in aggressive marketing and mass mailing operations.
The threat actor is looking for someone capable of reaching target audiences through channels such as Telegram, WhatsApp, Viber, and email, with a focus on efficiency. Responsibilities include managing bulk messaging campaigns, sourcing mailing databases with an emphasis on Central Asia, and developing unconventional marketing strategies.
The wording of the post indicates a shift in cybercriminal tactics, as threat actors increasingly adopt professional marketing methods to expand their reach. The focus on “innovative” and “aggressive” strategies suggests a willingness to cross ethical and legal boundaries. By targeting individuals skilled in data acquisition and digital outreach, the threat actor appears to be building a team capable of executing high-volume campaigns involving phishing, scams, or malware distribution.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.
Article Link: https://socradar.io/bank-banten-deloitte-source-code-totalenergies-france/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics

