Alleged SeAH, Under Armour, SecureTeen, and Cloudeka Data Exposures Detected
Alleged SeAH, Under Armour, SecureTeen, and Cloudeka Data Exposures Detected
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
SOCRadar’s Dark Web Team identified several high-impact underground posts this week, including alleged leaks involving SeAH Holdings, Under Armour, SecureTeen, and Indonesian cloud provider Cloudeka. Threat actors claimed supply chain compromise, ransomware-driven publication, credential databases, and source-code exposure across these incidents. All information comes directly from actor listings and remains unverified, but the nature of the alleged data, ranging from API keys to customer PII, highlights ongoing risks across industrial, retail, parental-control, and cloud service ecosystems.a
Receive a Free Dark Web Report for Your Organization:
The Alleged Data of SeAH Holdings are Leaked

The SOCRadar Dark Web Team has identified a new post alleging a significant data leak targeting SeAH Holdings, a prominent South Korean conglomerate specializing in global steel manufacturing. The threat actor asserts that this incident, purportedly dating to November 2025, stems from a supply chain attack involving a compromised third-party contractor rather than a direct intrusion into the company’s core network.
According to the unverified claims found on the Dark Web, the leaked dataset purportedly exposes critical technical assets belonging to the industrial group. The actor lists Source Code, Configuration Files, and sensitive Hardcoded Credentials among the compromised data. Furthermore, the leak allegedly contains valid Application Programming Interface (API) Keys.
If these allegations regarding the SeAH Holdings data breach are proven accurate, they underscore the critical importance of third-party risk management. The potential exposure of API Keys and Hardcoded Credentials presents a severe security risk, as such data can often provide attackers with persistent, unauthorized access to sensitive corporate environments, bypassing traditional perimeter defenses.
The Alleged Database of Under Armour is Leaked
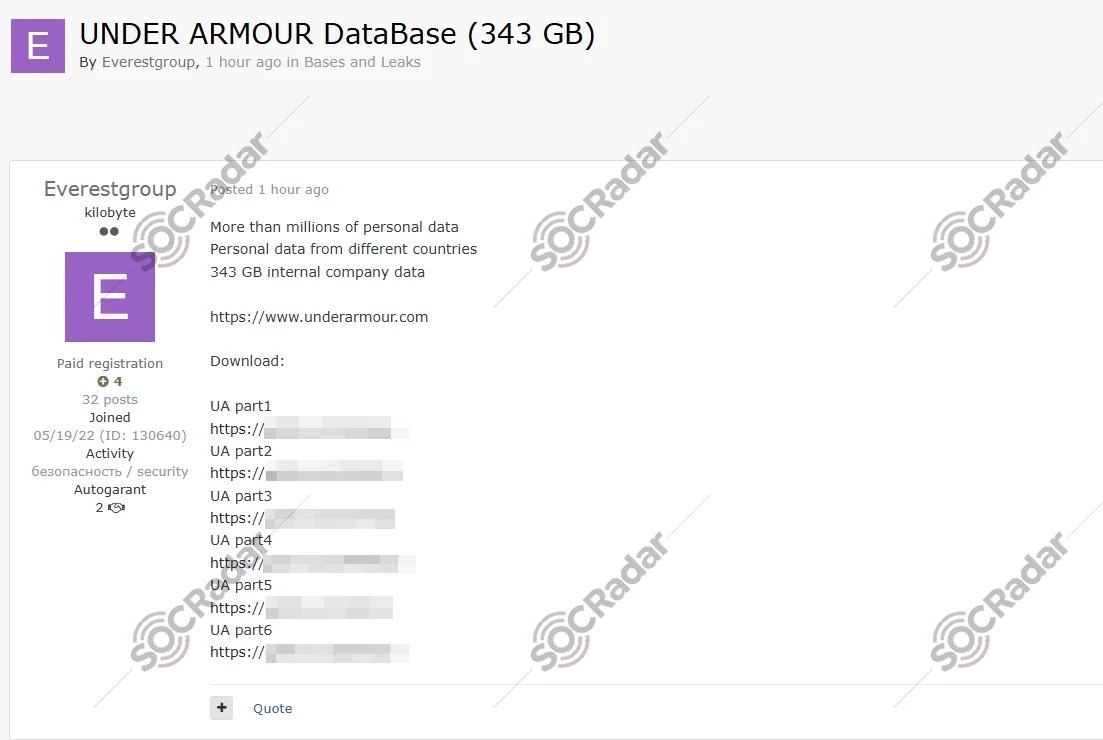
The SOCRadar Dark Web Team has been monitoring a critical incident involving Under Armour, the globally recognized US-based manufacturer of athletic footwear and performance apparel. The Everest Ransomware gang is known for its double-extortion tactics and has purportedly released a massive 343 GB dataset on a Russian-speaking hacker forum.
The incident followed a precise timeline of extortion. Everest Ransomware initially listed the company on their TOR-based Data Leak Site (DLS) on November 17, 2025. They threatened publication if their demands were not met. Following the expiration of their 7-day deadline, the group executed their threat and published the download links on the hacker forum on November 24, 2025.
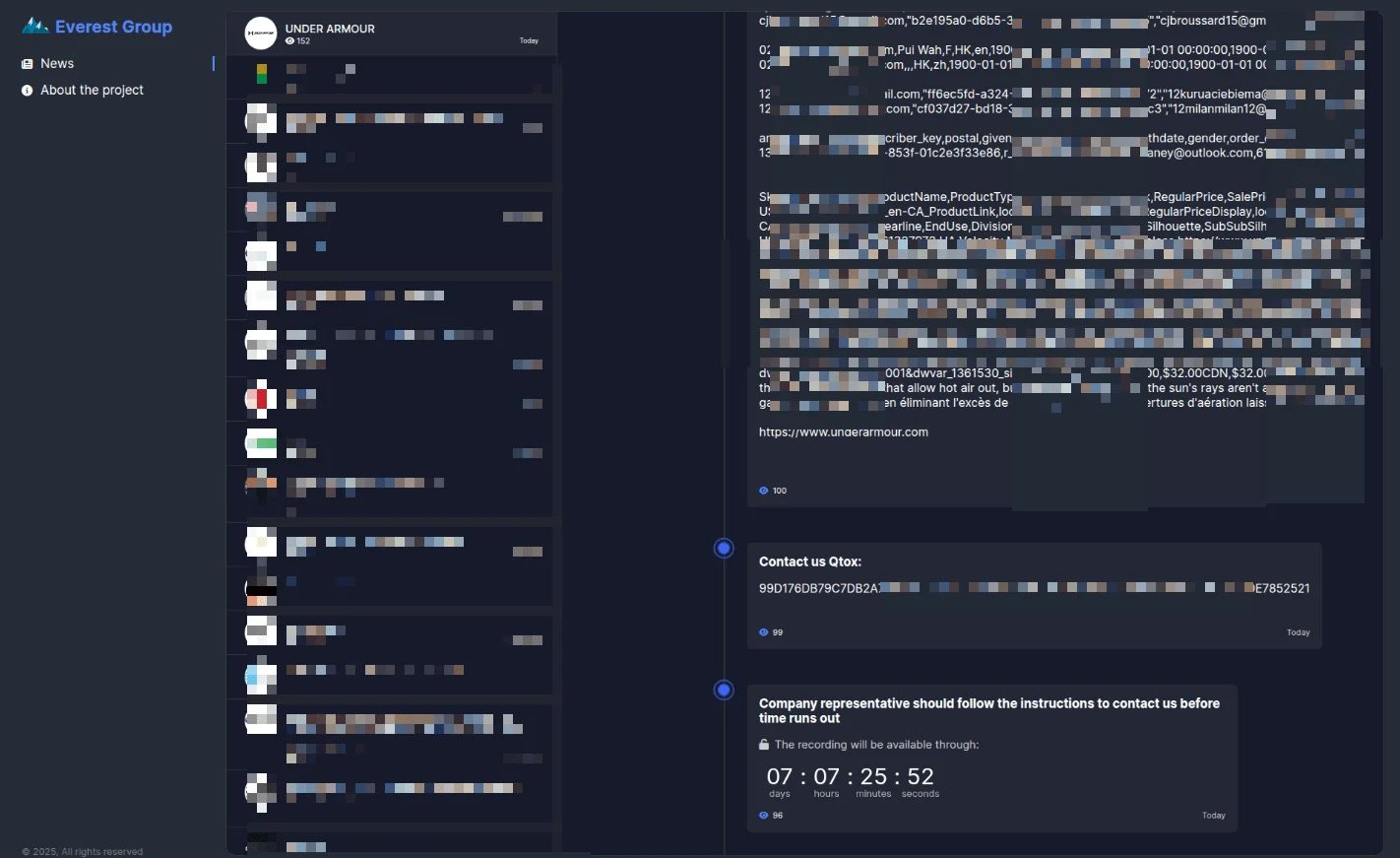
While the final forum post was brief, the original listing provided granular details regarding the compromised assets. The leak allegedly contains Customer Personally Identifiable Information (PII) combined with extensive shopping history. This includes email addresses, phone numbers, purchase timestamps, store preference records, and location data. Furthermore, the samples indicated the exfiltration of sensitive business intelligence, such as marketing campaign logs, deep link tracking entries, and detailed product catalog records directly linked to customer profiles.
Notably, this is not the first major security incident associated with Under Armour. In February 2018, the company suffered a massive data breach affecting its subsidiary app, MyFitnessPal. That incident compromised approximately 150 million user accounts, exposing usernames, IP addresses, email addresses, and hashed passwords.
The Alleged Database of SecureTeen is on Sale
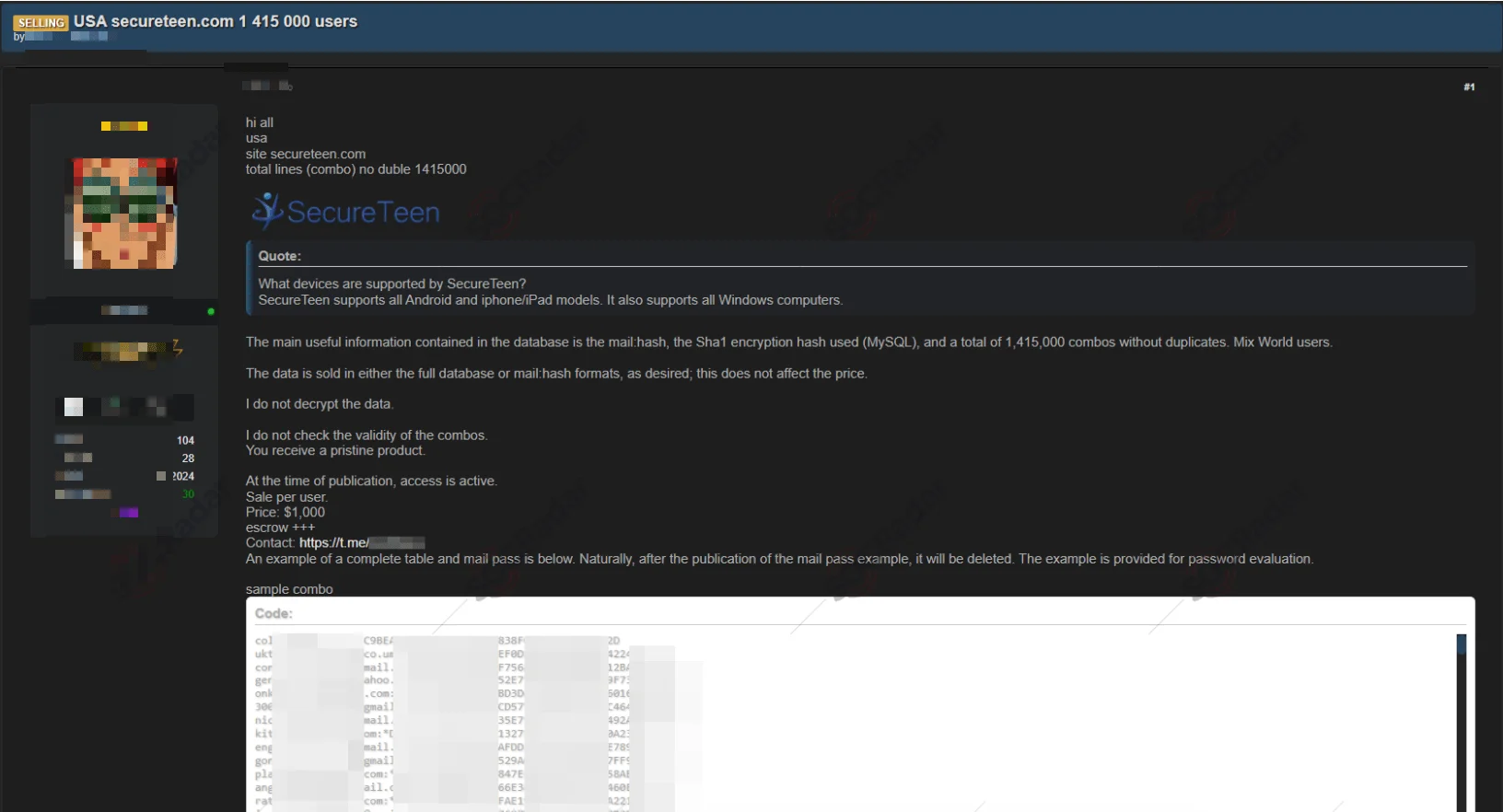
The SOCRadar Dark Web Team has identified a concerning new post on an underground forum where a threat actor is attempting to sell a database allegedly belonging to SecureTeen. SecureTeen is a well-known parental control software provider that allows parents to monitor and manage their children’s activities on Android, iOS, and Windows devices.
The threat actor claims to possess a database containing approximately 1.4 million unique records (1,415,000 lines). The seller explicitly states that the data originates from the USA and includes user credentials formatted as email:hash. The password hashes are allegedly encrypted using SHA1 (MySQL), which is considered an outdated and vulnerable hashing algorithm by modern standards.
According to the listing, the dataset is being offered for a price of $1,000. The actor emphasizes that they are selling the data “as is” without decryption but guarantees that access is currently active. The sale includes options for purchasing the full database or specific “mail:hash” formats, with the transaction facilitated via escrow services.
This alleged breach is particularly alarming given the sensitive nature of SecureTeen’s business. Parental control apps collect highly invasive data, including real-time location, SMS logs, call history, and app usage to function. While the seller currently mentions only credential pairs (combos) and hashes, unauthorized access to parent accounts could theoretically allow a threat actor to view the monitored activities of minors. Furthermore, the use of SHA1 hashing, if true, suggests that the passwords could be cracked relatively quickly, putting users who reuse passwords across services at immediate risk.
The Alleged Database of Cloudeka is Leaked

The SOCRadar Dark Web Team has detected a new data leak claim targeting Lintasarta Cloudeka, an Indonesian cloud service provider established in 2010.The firm provides cloud services aimed at both small-medium enterprises and large corporations in the region.
A threat actor has posted on a Dark Web forum, claiming to have breached the company’s systems in November 2025. Unlike typical customer database leaks, this incident reportedly involves the theft of the platform’s Source Code. The actor has allegedly made the data available for download to prove the compromise.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.
Article Link: https://socradar.io/seah-under-armour-secureteen-cloudek-data-breach/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics

