CVE-2026-20045 Actively Exploited Cisco Unified Communications Zero-Day Explained
CVE-2026-20045 Actively Exploited Cisco Unified Communications Zero-Day Explained
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
In late January 2026, Cisco released emergency patches for CVE-2026-20045, a critical Remote Code Execution (RCE) vulnerability affecting its Unified Communications products. The issue has been confirmed as actively exploited in real-world attacks. Several widely deployed collaboration and calling platforms are impacted, including Unified Communications Manager (Unified CM) and Webex Calling environments.
The vulnerability allows unauthenticated attackers on the network to send specially crafted HTTP requests to a device’s web-based management interface. If successfully exploited, these requests can trigger arbitrary command execution on the system. Attackers may initially gain user-level access and then escalate privileges to obtain full root control of the underlying operating system.
What Exactly Is CVE-2026-20045?
CVE-2026-20045 is a critical remote code execution vulnerability caused by improper validation of user-supplied input in HTTP requests sent to Cisco Unified Communications management interfaces.
Because the affected software does not adequately sanitize request data, an unauthenticated remote attacker can inject malicious input that results in arbitrary command execution. This means an attacker does not need valid credentials to exploit the flaw.
Cisco assigned the vulnerability a CVSS v3.1 score of 8.2, which technically falls within the High severity range. However, Cisco has described the issue as Critical because successful exploitation can allow an attacker to elevate privileges to root, resulting in full system compromise.
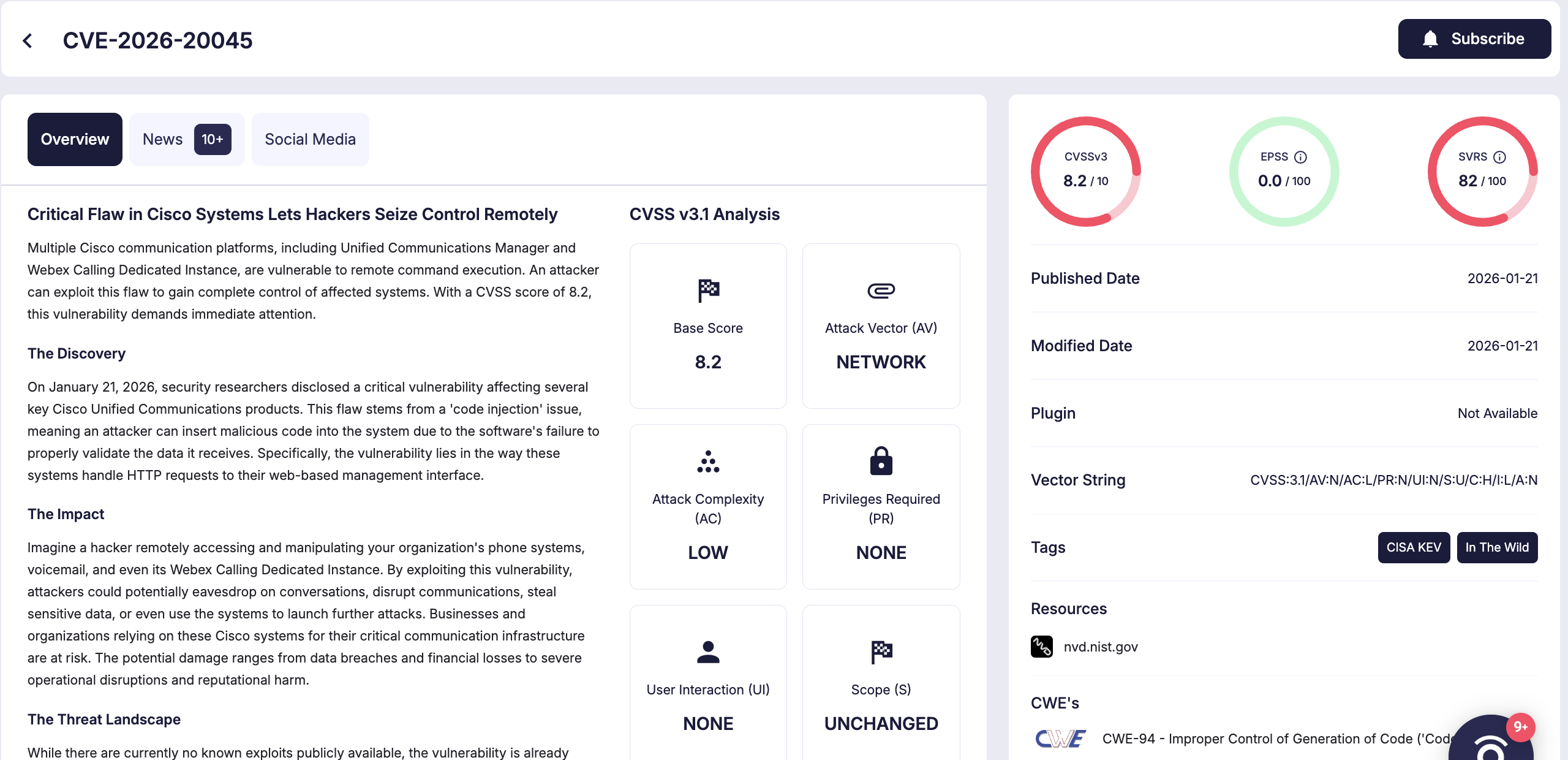
Details of CVE-2026-20045 (SOCRadar Vulnerability Intelligence)
Which Cisco Products Are Affected?
The vulnerability affects multiple Cisco Unified Communications solutions, including:
- Cisco Unified Communications Manager (Unified CM)
- Unified CM Session Management Edition (SME)
- Unified CM IM and Presence Service
- Cisco Unity Connection
- Webex Calling Dedicated Instance
These platforms are commonly used across enterprise voice, video, messaging, and presence deployments, making the vulnerability relevant to organizations running Cisco Unified Communications infrastructure in production environments.
How Is the Vulnerability Being Exploited in the Wild?
Cisco and independent security researchers have confirmed that CVE-2026-20045 was exploited by threat actors before patches were publicly available, qualifying it as a zero-day vulnerability. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the flaw to its Known Exploited Vulnerabilities (KEV) Catalog, validating active exploitation and requiring U.S. federal agencies to remediate affected systems by February 11, 2026.
Although public reports have not attributed the activity to a specific threat group, the observed exploitation behavior points to attackers scanning for exposed or poorly secured Unified Communications management interfaces and abusing unauthenticated HTTP access to gain a foothold.
What Should Organizations Do Right Now?
Cisco has released security updates to address CVE-2026-20045, and applying these patches should be treated as an immediate priority.
Security teams should consider the following actions:
- Apply available patches to all affected Unified CM, Unity Connection, and Webex Calling Dedicated Instance systems.
- Restrict access to management interfaces by using firewall rules, network segmentation, or access control lists.
- Review logs for unusual or suspicious HTTP requests targeting Unified Communications services.
- Avoid exposing management interfaces to the internet unless absolutely necessary, and limit access using IP allowlists when exposure cannot be avoided.
Because exploitation does not require authentication, systems that are publicly reachable or accessible from untrusted networks face a significantly higher risk.
SOCRadar’s Vulnerability Intelligence
For security teams tracking critical vulnerabilities like CVE-2026-20045, platforms such as SOCRadar can help provide additional context and visibility. By combining Cyber Threat Intelligence and Attack Surface Management (ASM)capabilities, organizations can more easily monitor newly disclosed vulnerabilities, identify potentially exposed assets, and prioritize remediation efforts based on real-world exploitation activity.
Why Does This Matter for Enterprise Security?
Unified Communications platforms support core business functions such as calling, messaging, meetings, and presence. A successful compromise can lead to service disruption, unauthorized access to internal systems, data exposure, or the deployment of persistent backdoors.
Since CVE-2026-20045 allows attackers to escalate privileges to root level, the impact extends beyond the affected application itself and can threaten connected systems within the enterprise environment. Timely patching, reduced attack surface exposure, and ongoing monitoring remain critical to limiting the risk posed by actively exploited vulnerabilities like this one.
Article Link: https://socradar.io/blog/cve-2026-20045-cisco-unified-communications-0-day/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics

