Oracle January 2026 CPU Delivers 337 Security Patches Including CVE-2025-66516 & CVE-2026-21962
Oracle January 2026 CPU Delivers 337 Security Patches Including CVE-2025-66516 & CVE-2026-21962
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Oracle has kicked off 2026 with a sizable security release that will immediately catch the attention of security teams. The January 2026 Critical Patch Update (CPU) delivers 337 new security patches spanning more than 30 Oracle product families, reflecting both the scale of Oracle’s ecosystem and the growing reliance on third-party components within enterprise software.
This blog provides a clear breakdown of what the January 2026 CPU includes, which vulnerabilities stand out, which products are most affected, and how organizations should approach remediation.
What Is Included in Oracle January 2026 CPU?
The January 2026 CPU resolves approximately 230 unique CVEs, distributed across 337 individual patches. The difference between these numbers is largely due to shared third-party libraries, where a single CVE may affect multiple Oracle products.
More than 235 of the patches address vulnerabilities that are remotely exploitable without authentication, significantly increasing their potential impact if left unpatched. Over two dozen vulnerabilities are rated critical, making this update particularly important for internet-facing systems.
Which Vulnerabilities Have the Highest CVSS Scores?
Oracle January 2026 CPU includes two vulnerabilities with maximum severity, both classified as remotely exploitable over HTTP without authentication.
CVE-2025-66516 (Apache Tika)
CVE-2025-66516 (CVSS 10.0 / 9.8 on NVD) is a critical vulnerability in the third-party Apache Tika library, which Oracle embeds in multiple products for document parsing and content extraction. The underlying Apache Tika issue was disclosed in 2025, and Oracle’s remediation expanded across later updates as additional product integrations were identified.
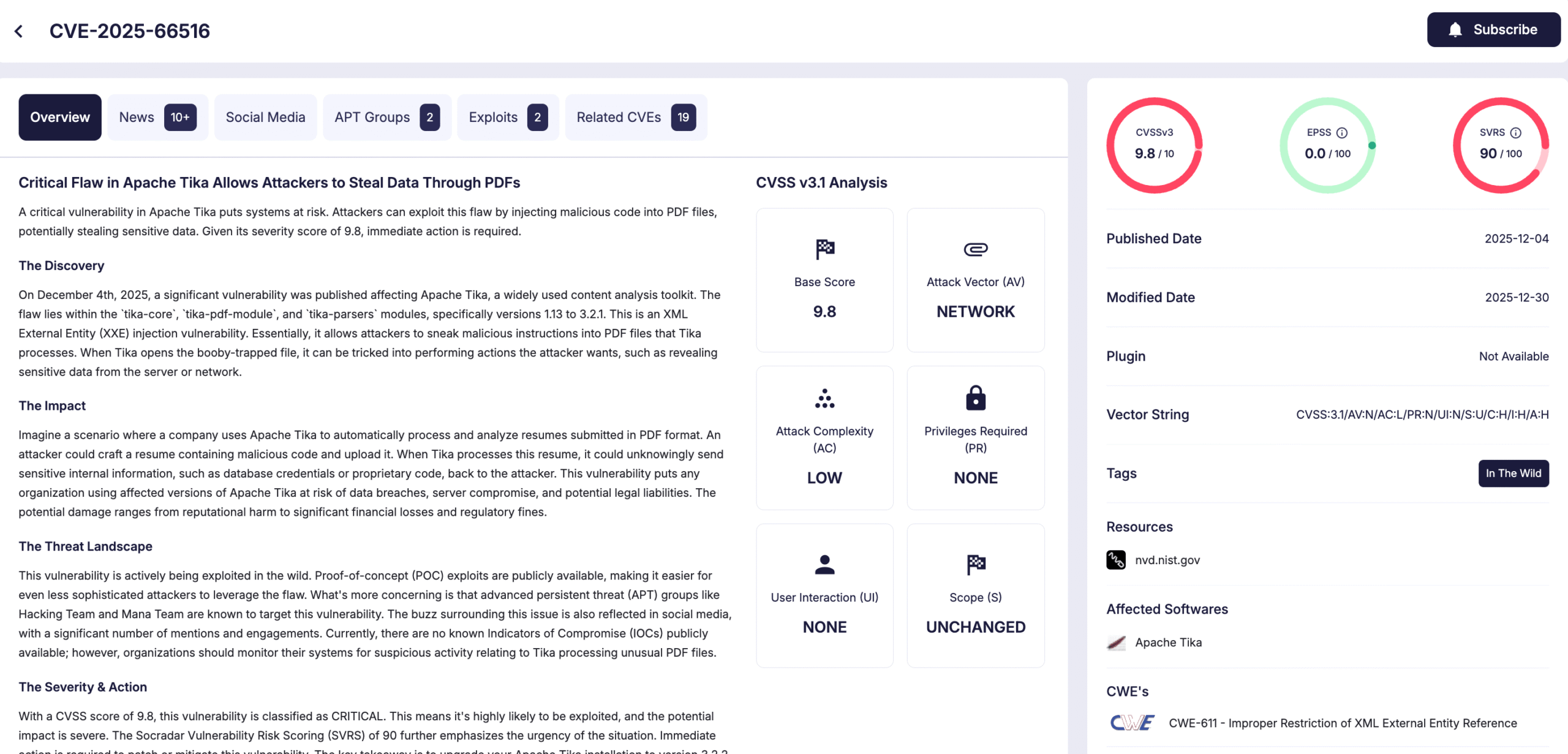
Details of CVE-2025-66516 (SOCRadar Vulnerability Intelligence)
In the January 2026 bulletin, Oracle lists CVE-2025-66516 with a CVSS score of 10.0 for multiple products, including:
- Oracle Business Process Management Suite — Runtime Engine (Apache Tika)
- Oracle Middleware Common Libraries and Tools — Third-party Apache Tika component
Because this CVE impacts shared libraries, organizations may need to apply patches across more than one Oracle product family to fully address the risk.
CVE-2026-21962 (WebLogic Server Proxy Plug-in)
CVE-2026-21962 (CVSS 10.0) affects the WebLogic Server Proxy Plug-in for both Apache HTTP Server and Microsoft IIS, and is listed under Oracle HTTP Server and Oracle WebLogic Server Proxy Plug-in. According to Oracle, affected supported versions include 12.2.1.4.0, 14.1.1.0.0, and 14.1.2.0.0.
Because proxy plug-ins commonly sit at the network edge, this vulnerability is particularly relevant for externally exposed Oracle HTTP Server and WebLogic deployments.
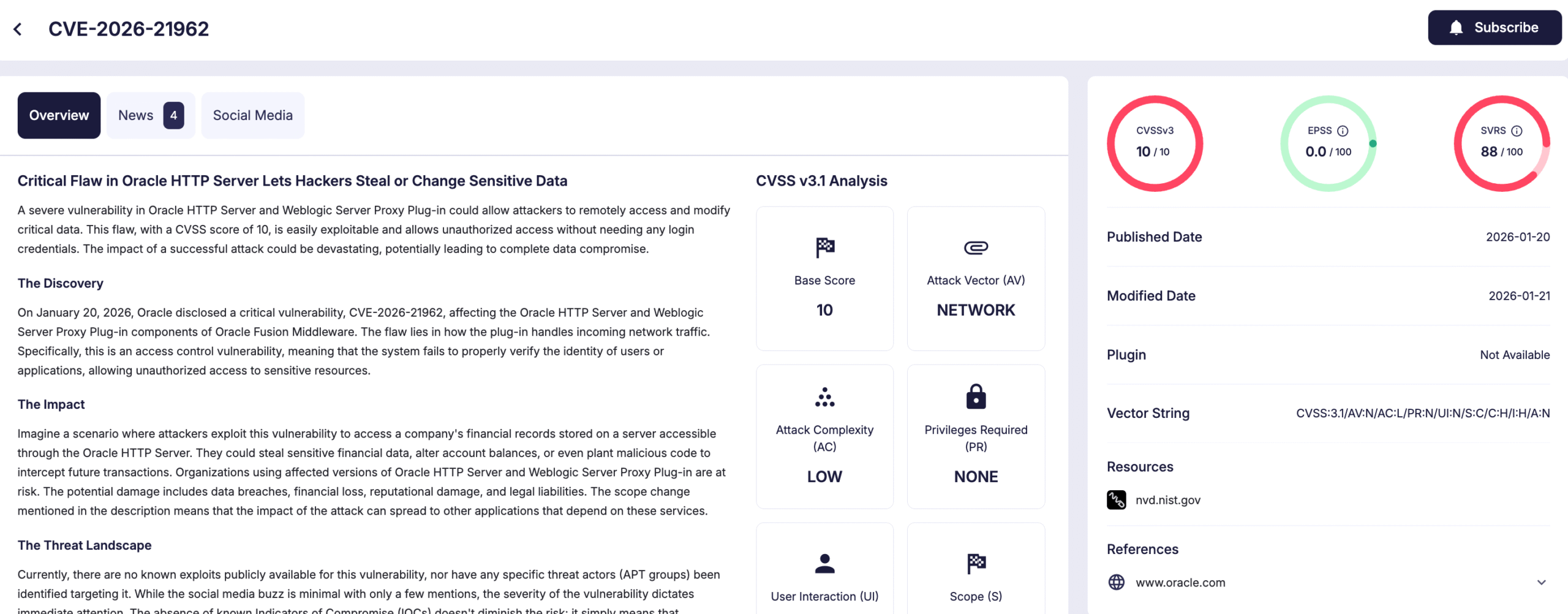
Details of CVE-2026-21962 (SOCRadar Vulnerability Intelligence)
Tracking critical vulnerabilities across many vendor advisories can be challenging. Brief, focused cyber threat intelligence can help security teams correlate these issues, affected products, and real-world exposure faster. Solutions such as SOCRadar’s Cyber Threat Intelligence module are designed to provide this context by continuously monitoring vulnerability disclosures, exploit trends, and vendor advisories in one place – supporting more informed patch prioritization.
Are Any of the Vulnerabilities Being Actively Exploited?
There are no known zero-day vulnerabilities in Oracle January 2026 CPU. That means none of the listed flaws are confirmed to be under active exploitation at the time of release.
However, Oracle notes that attackers have previously succeeded in exploiting vulnerabilities after patches were released but not applied, and continues to recommend timely deployment of CPU updates. The absence of active exploitation should be seen as a window of opportunity rather than a reason to postpone updates.
Which Oracle Products Require the Most Attention?
Several product families stand out due to the volume and nature of fixes:
- Oracle Communications leads with 56 patches, 34 of which address remotely exploitable issues.
- Fusion Middleware follows closely with 51 patches, including 47 remotely exploitable without authentication.
- Financial Services Applications received 38 patches, most of them remotely exploitable.
- MySQL, Java SE, PeopleSoft, and Hyperion also saw notable updates affecting core enterprise deployments.
The wide distribution of patches means most organizations will need a coordinated, cross-team approach rather than isolated fixes.
How Should Organizations Prioritize Patching?
Given the size of this update, prioritization is essential. Security teams should focus first on:
- Critical-severity issues, especially those with CVSS scores close to or at 10.0.
- Internet-facing systems and services exposed to untrusted input.
- Products that rely heavily on shared third-party libraries, as these issues often have broader blast radiuses.
Testing patches in staging environments remains important, but delays should be kept to a minimum for high-risk systems.
For detailed patch matrices, CVE mappings, and product-specific guidance, review Oracle’s official January 2026 Critical Patch Update advisory.
Enhance Patch Decisions With SOCRadar
Managing large-scale patch cycles requires visibility beyond individual advisories. SOCRadar’s Cyber Threat Intelligence (CTI) and Attack Surface Management (ASM) modules work together to help security teams prioritize and act faster.
SOCRadar’s Vulnerability Intelligence, CTI module
Key capabilities include:
- Real-time monitoring of vulnerability disclosures and exploit activity
- Correlation of CVEs with threat actor activity and emerging attack trends
- Continuous discovery of internet-facing assets and exposed services
- Identification of vulnerable and misconfigured systems across the external attack surface
By combining threat context with asset visibility, organizations can better assess risk and focus remediation efforts where they matter most.
Article Link: https://socradar.io/blog/oracle-january-2026-cpu-337-security-patches/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics


