Top 10 Ransomware Groups of 2025
Top 10 Ransomware Groups of 2025
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
The Top 10 Ransomware Groups of 2025 illustrate how the ransomware ecosystem changed in structure rather than simply growing in volume. After the disruption of dominant groups in 2024, the ecosystem entered 2025 without a clear center of gravity. Instead of collapsing, ransomware operations adapted. Affiliates became more independent, group boundaries blurred, and former rivals increasingly operated without strict competitive lines. This shift reshaped how campaigns were organized, how infrastructure was shared, and how ransomware operations sustained momentum.
As the year progressed, ransomware activity became more fragmented and less centralized. Traditional Ransomware-as-a-Service models steadily lost influence as affiliates rotated between groups, reused the same tooling across multiple brands, and shifted loyalties based on reliability rather than reputation. While this reduced the dominance of individual groups, it made attribution, tracking, and disruption significantly harder for defenders.
The impact on victims remained severe. According to Fortinet, 73% of organizations experienced at least one ransomware incident, yet paying a ransom rarely meant full recovery. On average, only 60% of data was restored after payment, and just 4% of victims recovered all of their data. At the same time, ransomware operations became quieter and more patient. Fortinet data shows that attackers often remained undetected for months, and in some cases longer than a year, allowing them to exfiltrate data, map internal dependencies, and apply pressure with far greater precision.
What are the Top 10 Ransomware Groups of 2025?
1. Scattered Lapsus$ Hunters
Scattered Lapsus$ Hunters earned the top position in 2025 by redefining what large-scale ransomware operations can look like without relying on software vulnerabilities. Rather than functioning as a conventional ransomware group, this alliance operated as a coordinated criminal ecosystem, openly uniting members and brands associated with Scattered Spider, LAPSUS$, and ShinyHunters. The decision to act publicly and collaboratively marked a clear break from traditional, siloed ransomware models.

Threat actor card of Scattered Lapsus$ Hunters
What set the group apart was its ability to scale attacks entirely through social engineering. The campaigns targeting enterprise SaaS environments, most notably Salesforce and later echoing access patterns seen in Salesloft Drift–related incidents, demonstrated how human workflows and identity trust could be weaponized at scale. Employees and contractors were contacted through highly polished vishing calls and guided through routine actions such as MFA resets or OAuth authorizations. By abusing connected-app approvals and long-lived OAuth tokens, the group bypassed MFA and gained persistent, programmatic access to sensitive corporate data. No platform vulnerabilities were exploited, reinforcing a core lesson of 2025: security posture can collapse even when systems are fully patched.
The group’s use of Telegram was central to its impact. Scattered Lapsus$ Hunters used the platform to apply public pressure, name executives, set ultimatums, and maintain attention through teaser posts. They also reused datasets from earlier incidents, including companies affected by the Snowflake breach, to strengthen their credibilitsnowy and promote their channels. At the same time, references to the ShinySp1d3r ransomware brand and SaaS supply-chain abuse signaled an evolution beyond data theft toward higher-impact ransomware operations.
Taken together, these factors explain why Scattered Lapsus$ Hunters stands at number one in 2025. The group did not dominate through encryption counts or headline ransom payments. Instead, it reshaped the threat landscape by proving that social engineering, identity abuse, and public psychological pressure can rival or surpass traditional ransomware techniques. In doing so, it offered a clear preview of where ransomware operations are heading next.
2. Qilin (Agenda) Ransomware
Qilin, also known as Agenda, ranked second in 2025 by combining extreme scale with operational discipline. While many ransomware groups struggled with takedowns or affiliate churn, Qilin expanded steadily throughout the year and surpassed 1,000 listed victims on its leak site. Activity was global, but most victims were concentrated in North America and Western Europe, with manufacturing, professional services, finance, and healthcare consistently targeted due to their low tolerance for disruption and regulatory exposure.

Threat actor card of Qilin (Agenda) ransomware
Qilin operated as a highly mature Ransomware-as-a-Service (RaaS) platform. Its encryptors, written in Go and Rust, supported Windows, Linux, and virtualized environments, enabling infrastructure-wide impact rather than endpoint-level damage. In 2025, investigations repeatedly showed Qilin gaining access through stolen credentials, VPN and RDP exposure, managed service providers, and remote monitoring tools, then moving laterally at speed. The group’s operational model favored coordinated campaigns, sometimes hitting dozens of organizations in the same sector or country within weeks, reinforcing its reputation as an industrial-scale ransomware operation.
What truly distinguished Qilin was how it professionalized extortion itself. In addition to data theft and encryption, the group integrated legal and psychological pressure into negotiations, including features such as a “call a lawyer” option that reframed ransom demands around regulatory fines and litigation risk. Threat intelligence also points to strong ties with Russian-speaking cybercrime ecosystems, including recruitment on closed forums such as RAMP (Russian Anonymous Market Place) and configuration rules excluding CIS targets. This blend of scale, structured coercion, and regional operating norms was most starkly illustrated by the Synnovis healthcare attack, which caused widespread hospital disruption and marked a rare moment where ransomware activity was publicly linked to patient harm.
3. Akira Ransomware
Akira Ransomware was one of the most stable and damaging ransomware groups of 2025, adding nearly 740 victims to its leak site over the year. While many groups struggled with takedowns or rebrands, Akira maintained a steady pace, focusing on industries where downtime is costly and tolerance for disruption is low. Manufacturing, healthcare, education, and professional services remained its core targets, mainly across North America and Europe. This consistency, rather than short-lived spikes, secured Akira’s place among the top ransomware groups of 2025.

Threat actor card of Akira Ransomware
From a technical perspective, Akira relied on well-documented but highly effective intrusion paths. CISA reporting highlights repeated exploitation of exposed or weakly protected perimeter systems, including CVE-2020-3259 and CVE-2023-20269 affecting Cisco VPN infrastructure, as well as CVE-2024-40766targeting SonicWall SMA devices. These attacks were often combined with stolen credentials and VPN access without MFA. Once inside, Akira followed a familiar but efficient playbook: lateral movement, backup targeting, data exfiltration, and encryption across Windows systems and virtualized environments such as VMware ESXi.
Geographically, Akira concentrated its operations in regions with high ransom payment capacity. North America remained the primary focus, with U.S.-based organizations accounting for the majority of victims. Europe also saw sustained pressure, particularly in the United Kingdom, Germany, France, and the Netherlands. In 2025, Switzerland stood out as a regional hotspot, where national authorities reported a sharp rise in Akira-related incidents affecting hundreds of companies. At the same time, attacks in Australia and the wider Asia-Pacific region showed that Akira continued to expand beyond its traditional Western focus.
What set Akira apart in 2025 was not only execution, but pressure. Negotiations were conducted in a calm, methodical tone, with operators presenting themselves as structured service providers rather than chaotic criminals. In several cases, victims reported receiving basic “security advice” or checklists after payment, a psychological tactic that reframed ransom demands as a transactional cost. When negotiations stalled, CISA described direct phone calls to executives and employees to spread panic beyond the IT team. Combined with its retro, command-line-style leak site that reinforced a distinct brand identity, this mix of technical reliability and psychological coercion made Akira one of the most effective ransomware operators of the year.
4. Cl0p Ransomware
Cl0p Ransomware, aka CLOP remained one of the most disruptive ransomware actors of 2025 by continuing its long-standing supply-chain-driven extortion strategy. Rather than chasing volume through affiliates, the group focused on scale, turning single points of failure into mass compromise events. Over the course of the year, Cl0p added more than 500 victims to its leak site, confirming its role as a campaign-oriented extortion actor.

Threat actor card of Cl0p Ransomware
Cl0p’s most visible operation in 2025 was its Oracle E-Business Suite (EBS) zero-day campaign. The group exploited CVE-2025-61882 and CVE-2025-61884, two high-impact flaws that allowed unauthenticated access to core EBS components and enabled rapid data theft without deploying ransomware. CISA later confirmed active exploitation by adding CVE-2025-61884 to the Known Exploited Vulnerabilities catalog. Within weeks, more than 100 organizations linked to Oracle EBS appeared on Cl0p’s leak site.
This activity followed the same playbook Cl0p used in its 2024 supply-chain campaigns, including MOVEit Transfer, GoAnywhere MFT, and Cleo. Across these operations, the group consistently favored encryption-less extortion, relying on large-scale data theft and controlled public leaks rather than disruptive payloads.
Cl0p’s effectiveness in 2025 came from restraint and precision. By targeting deeply embedded enterprise software and exploiting trust relationships, the group achieved high leverage with minimal operational exposure. The Oracle EBS campaign was not an anomaly but a continuation of a mature strategy that keeps Cl0p among the most strategically dangerous ransomware actors in the ecosystem.
5. DragonForce Ransomware
DragonForce Ransomware rose sharply in 2025 by changing how ransomware operations are structured. Instead of a classic RaaS model, the group shifted to a decentralized cartel approach. Affiliates were allowed to run their own branding and binaries while relying on DragonForce infrastructure, which made attribution harder and reduced the impact of law enforcement actions since there was no single brand or control point to shut down. During the year, the group added more than 200 victims to its leak site, but its prominence was not driven by victim volume alone. DragonForce also became highly active on the RAMP forum, a key marketplace for ransomware affiliates, to the point where the forum’s logo was temporarily replaced with DragonForce branding, signaling its influence and visibility within the ransomware

Threat actor card of DragonForce Ransomware
Technically, DragonForce combined familiar intrusion methods with effective defense bypass. The group actively used BYOVD (Bring Your Own Vulnerable Driver) attacks, loading legitimate but vulnerable kernel drivers to disable antivirus and EDR tools before encryption. This allowed them to blind security products at kernel level rather than fighting detections in user space. In parallel, DragonForce exploited supply-chain trust, most notably through SimpleHelp RMM, abusing CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728 to compromise MSP environments and push ransomware to downstream customers.
In several cases, DragonForce affiliates leveraged Log4j (CVE-2021-44228), a vulnerability whose disclosure had already exposed how quickly widely deployed software flaws could be turned into large-scale compromise.
DragonForce also benefited from clear relationships inside the ransomware ecosystem. It absorbed former RansomHub affiliates after that group went dark, reused leaked LockBit and Conti codebases, and partnered operationally with access-focused actors such as Scattered Spider in several high-impact campaigns. In these cases, DragonForce provided the ransomware and extortion framework, while partners handled initial access and social engineering. This mix of cartel structure, reliable tooling, and cooperative operations explains why DragonForce became one of the most visible and disruptive ransomware groups of 2025.
6. Play Ransomware
Play Ransomware remained one of the more consistent ransomware actors in 2025, relying on steady operations rather than hype-driven campaigns. Active since 2022, the group transitioned toward a Ransomware-as-a-Service structure by late 2023, which helped standardize its tooling and scale operations. In 2025 alone, Play added more than 350 victims to its leak site, confirming that its relevance came from sustained activity rather than short-term spikes.
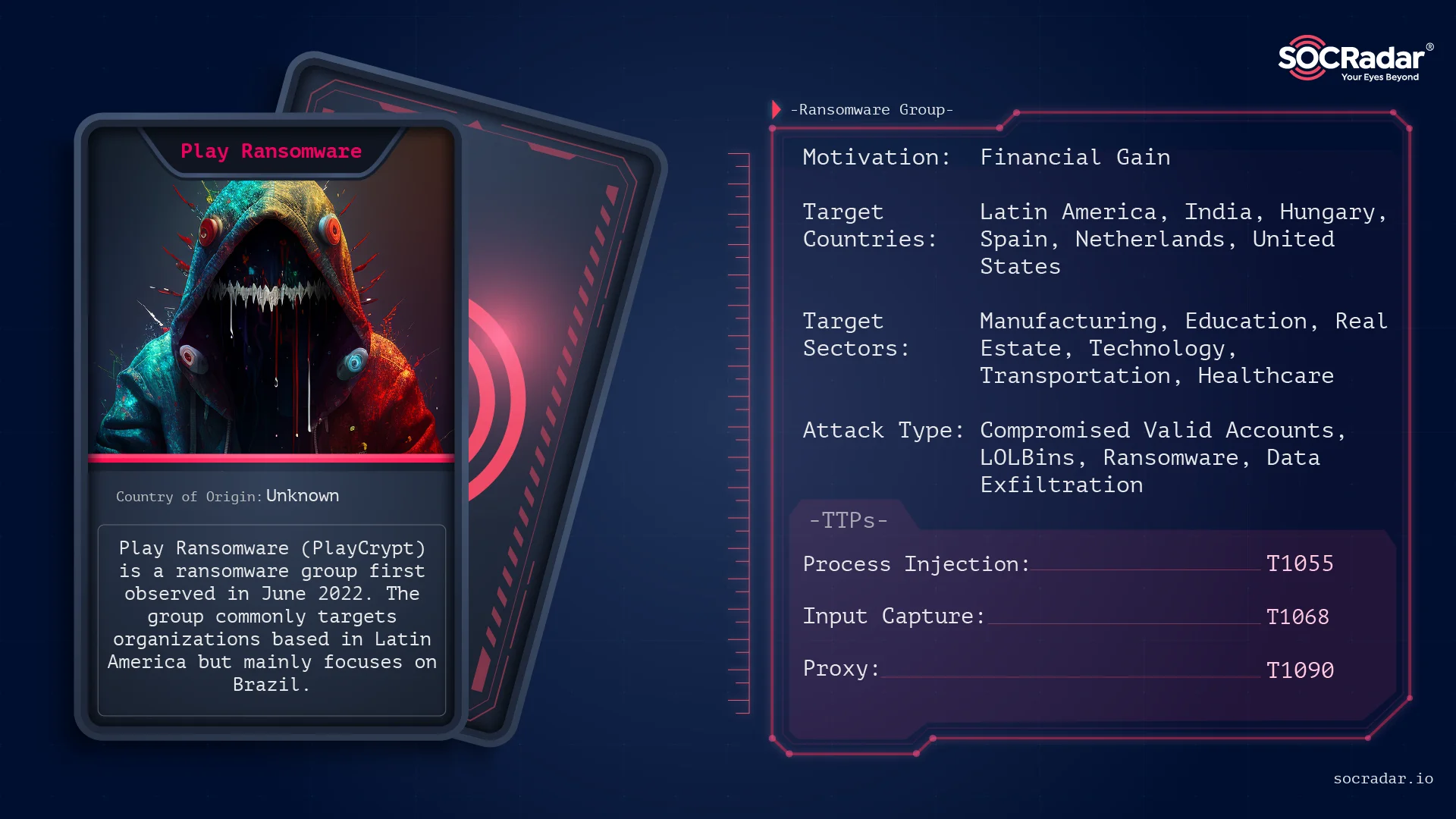
Threat actor card of Play Ransomware
Operationally, Play focused on hands-on intrusions and trusted-access abuse. Initial access commonly relied on valid credentials, exposed RDP services, and known FortiOS vulnerabilities such as CVE-2018-13379 and CVE-2020-12812. After entry, operators moved laterally using built-in system tools and distributed payloads through mechanisms like Group Policy, scheduled tasks, and PsExec. One of the group’s defining traits was its use of intermittent encryption, which encrypted only parts of files to reduce detection while still disrupting operations.
Over time, Play expanded its scope beyond Windows environments. The introduction of a Linux variant capable of targeting VMware ESXi systems marked a shift toward higher-impact infrastructure attacks. The group consistently targeted IT service providers, cloud firms, and organizations with downstream dependencies, increasing the blast radius of each incident. While Play avoided the cartel-style branding seen in 2025, its technical maturity, cross-platform capability, and growing victim list secured its place among the notable ransomware groups of the year.
7. SafePay Ransomware
SafePay Ransomware became one of the most active ransomware groups of 2025, adding more than 340 victims to its leak site within a single year. First observed around September 2024, SafePay moved quickly from a low-profile operation to a high-volume threat actor. Unlike many competitors, the group does not appear to rely on a classic Ransomware-as-a-Service model. The same core operators seem to manage intrusion, encryption, and extortion, which gives SafePay tighter control over campaigns and victim handling.

Threat actor card of SafePay Ransomware
SafePay follows a well-structured double extortion model. After gaining access, the group steals sensitive data and later encrypts systems, threatening public disclosure through its Dark Web leak site if payment is refused. Initial access is commonly achieved through stolen credentials, exposed VPN or RDP services, and social engineering techniques that combine phishing with direct interaction, such as fake IT support calls. In several incidents, attackers bypassed MFA due to weak configurations rather than technical exploits.
A notable operational trait is SafePay’s deliberate avoidance of CIS countries. The ransomware checks system language settings and terminates execution if it detects Russian or related regional languages. This behavior, combined with victim distribution patterns, strongly suggests intentional geofencing rather than technical limitation. Most victims are located in the United States and Western Europe, with manufacturing, technology, education, healthcare, and business services among the most affected sectors.
SafePay’s rise into the Top 10 ransomware groups is driven by scale rather than innovation. While its techniques rely on familiar tools such as PowerShell, Mimikatz, RDP, WinRAR, and Rclone, the group compensates with aggressive operations, fast execution, and consistent victim listings. In 2025, SafePay stood out not for novel malware design but for its ability to sustain pressure across hundreds of organizations, making it one of the most impactful ransomware actors of the year.
8. INC Ransom
INC Ransom emerged as one of the fastest-growing ransomware operations in 2025 and secured a place among the top groups by activity. Throughout the year, the group added more tha 380 victims to its leak site, showing both scale and consistency rather than short-lived spikes.
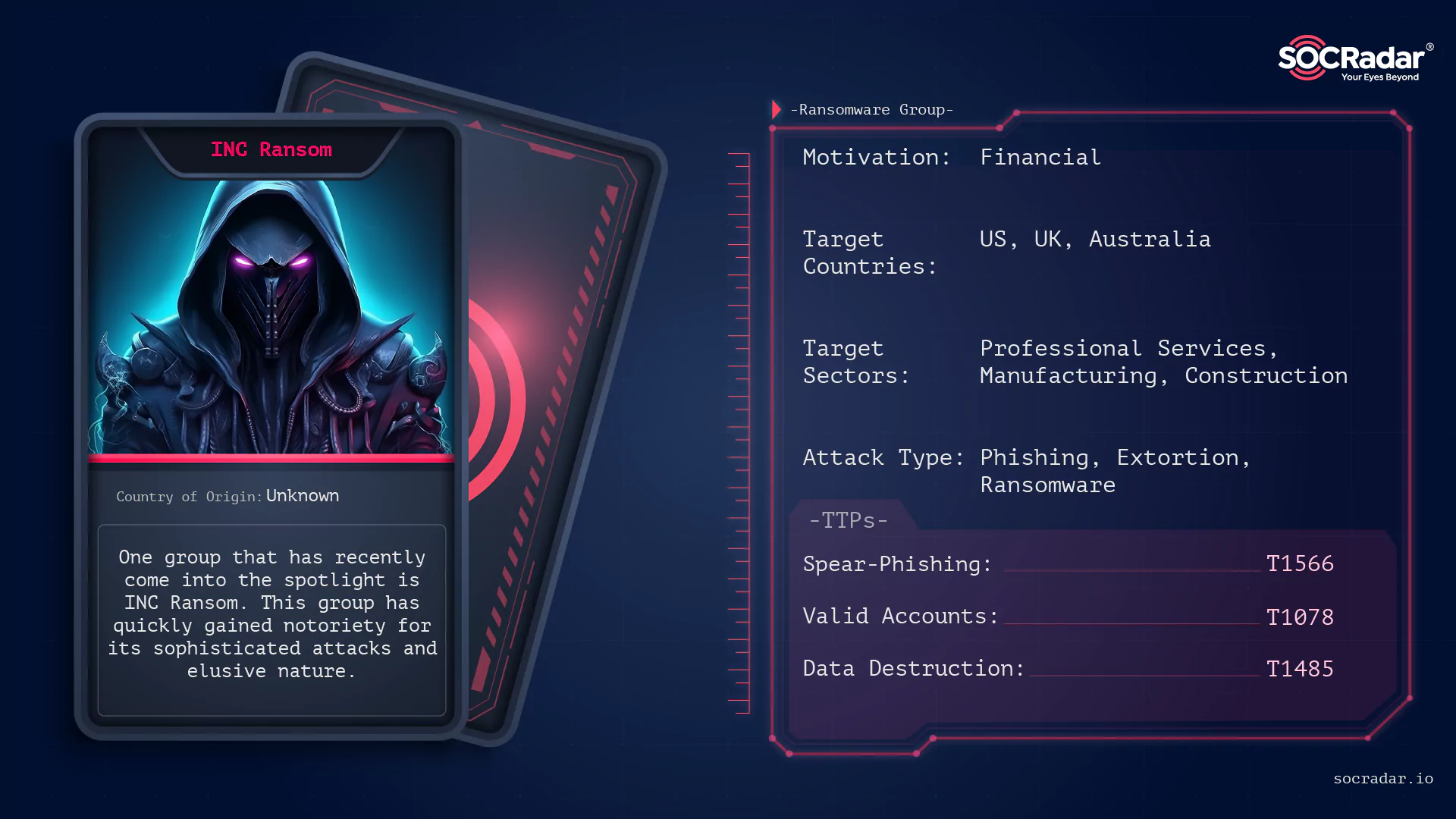
Threat actor card of INC Ransom
INC Ransom operates with a targeted approach instead of broad opportunistic campaigns. The group mainly focuses on corporate networks with high financial capacity and sensitive data. Initial access often relies on spear-phishing and exploitation of known enterprise-facing vulnerabilities, most notably CVE-2023-3519 affecting Citrix NetScaler. After gaining access, operators rely heavily on legitimate tools and LOLBins for reconnaissance, lateral movement, and credential access, which helps them blend into normal network activity.
The group follows a classic double-extortion model. Data is exfiltrated before encryption, and victims are pressured with the threat of public leaks through INC’s dedicated leak infrastructure. Their operations show strong hands-on activity: operators manually deploy ransomware using tools such as WMIC and PsExec, troubleshoot failed executions, and adapt during live intrusions. This level of interaction, combined with steady victim growth in 2025, positions INC Ransom as a mature and persistent threat rather than an experimental or short-term operation within the ransomware ecosystem.
9. Lynx Ransomware
Lynx Ransomware secured its place among the top ransomware groups of 2025 by scaling fast and capitalizing on the momentum created by INC. Emerging in mid-2024, Lynx is widely assessed as a rebrand or offshoot of the INC operation, built on shared source code and a similar operational model. In 2025 alone, the group added more than 250 victims to its leak site, pushing its total close to 300 and demonstrating sustained activity rather than a short-lived spike.

Threat actor card of Lynx Ransomware
Lynx operates under a structured Ransomware-as-a-Service model and actively recruits affiliates through underground forums such as RAMP. Affiliates are provided with ready-to-use Windows, Linux, and ESXi payloads, a negotiation panel, and leak-site publication tooling. The overlap with INC is not only organizational but also technical, with large portions of code reused, especially in Linux and ESXi variants. This continuity allowed Lynx to mature quickly without the trial-and-error phase seen in many new ransomware brands.
What distinguishes Lynx in 2025 is consistency. The group focuses heavily on manufacturing, business services, and technology firms, with the United States as the primary geographic target, followed by Western Europe and Australia. Operations emphasize double extortion, rapid encryption, and public leak pressure rather than prolonged negotiations. In the broader 2025 landscape, Lynx reflects a clear trend: established ransomware ecosystems fragmenting into parallel brands that share affiliates, tooling, and experience, while maintaining separate identities to reduce risk and extend operational lifespan.
10. RansomHub
RansomHub became one of the most visible ransomware operations of 2025 by scaling at an unusually rapid pace. In a short time frame, the group added more than 230 victims to its leak site, which alone placed it among the most active ransomware groups of the year. This rapid expansion was striking not only because of its volume, but also because it occurred while the group was still establishing itself as a relatively new actor in the ecosystem.

Threat actor card of RansomHub
RansomHub operated with a classic RaaS structure but made itself attractive to affiliates through generous revenue sharing and fast payouts. Much of its affiliate recruitment and coordination activity took place on the RAMP forum, where the group remained highly active. Its campaigns relied on familiar intrusion paths such as credential abuse, exposed remote services, and the exploitation of well-known vulnerabilities, including ZeroLogon (CVE-2020-1472), which had long been recognized in the security community for its severe impact on domain environments.
The group’s rise also fueled discussion around possible connections to LockBit. After sustained law enforcement pressure weakened LockBit, multiple signals suggested that former LockBit affiliates migrated toward RansomHub. Overlaps in tooling, operational style, and forum behavior supported this interpretation. Still, RansomHub did not position itself as a direct rebrand. Instead, it appeared to act as a transition point, absorbing experienced affiliates and filling the market gap left by declining major players.
Despite its momentum, RansomHub’s trajectory ended abruptly. In April 2025, claims of an exit scam surfaced, and shortly afterward, the group disappeared from underground channels and its infrastructure went silent. The combination of rapid growth, a large victim count, and sudden disappearance made RansomHub one of the most notable and short-lived ransomware operations of the year.
Bonus: LockBit
LockBit still deserves attention in 2025, even though it no longer ranks among the most active groups by victim count. For years, LockBit shaped the ransomware ecosystem through a mature Ransomware-as-a-Service model and a large affiliate base. That position was heavily damaged in February 2024, when Operation Cronos seized infrastructure, exposed internal data, and disrupted affiliate trust. After that point, many analysts considered LockBit effectively dismantled.
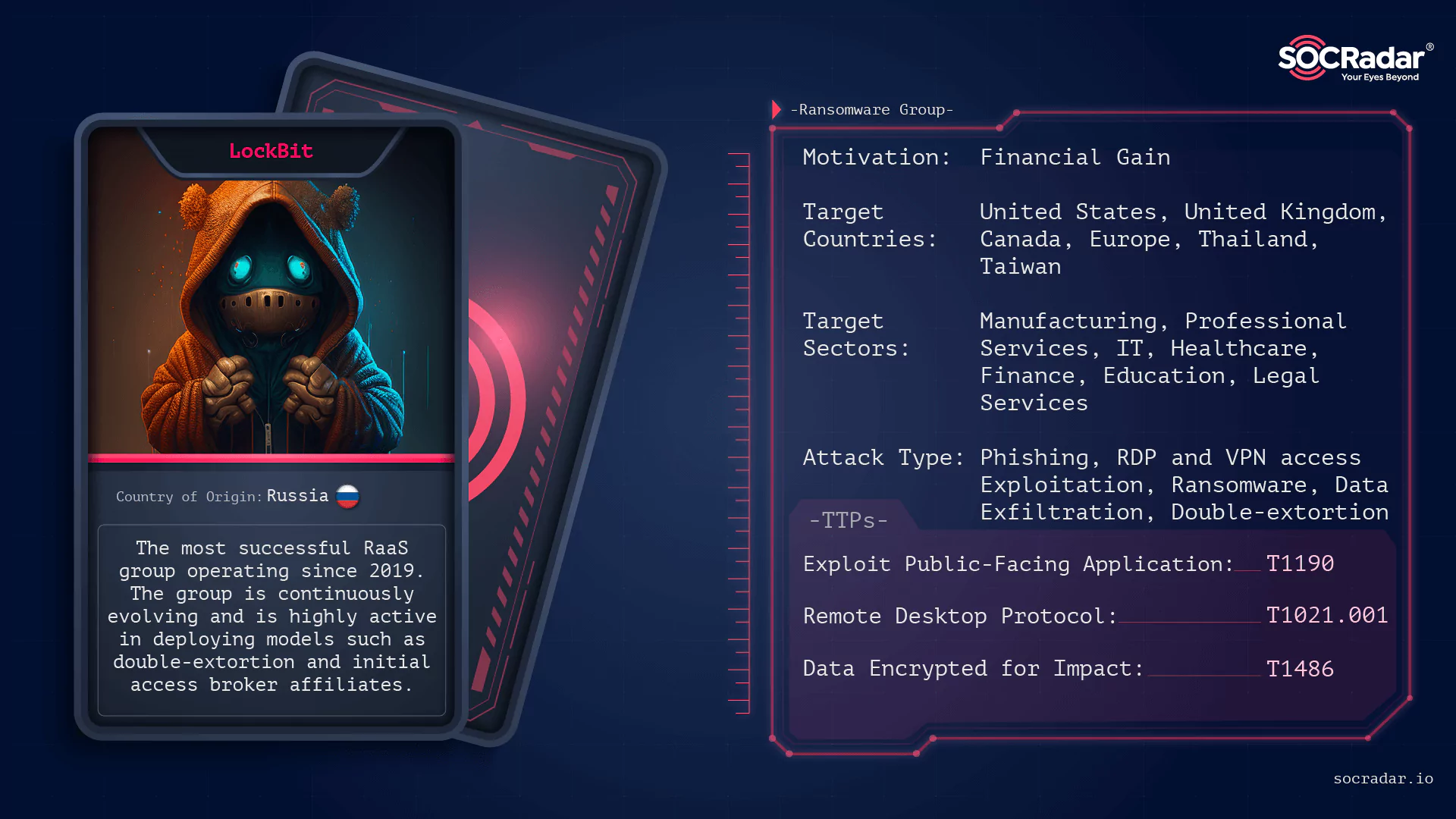
Threat actor card of LockBit
Despite this setback, LockBit has not fully exited the scene. In late 2025, the group announced LockBit 5.0, presenting it as a redesigned platform rather than a routine update. The new version emphasized modularity, faster encryption, and renewed affiliate incentives, signaling an attempt to reestablish relevance after losing ground to newer groups. The portal design, negotiation flow, and cryptocurrency handling closely mirror earlier LockBit versions, suggesting continuity with past operations, whether driven by surviving core members or actors reusing the brand.
At the same time, LockBit appeared in broader underground discussions about coordination between major ransomware groups. Cartel-style proposals involving actors like DragonForce and Qilin indicate a shift toward cooperation instead of competition. However, LockBit’s comeback has shown weaknesses. Its newly announced “secure” leak infrastructure was exposed shortly after launch, revealing reused servers and operational flaws. As a result, LockBit’s current role is less about volume and more about influence. Even as a “bonus” entry, LockBit remains important due to its reputation, legacy tooling, and continued efforts to adapt after disruption.
Conclusion
The ransomware activity observed throughout 2025 shows that the threat did not weaken after major takedowns, it reorganized. The fall of dominant groups accelerated fragmentation, collaboration, and specialization. Data-first extortion, identity abuse, and supply chain compromise became standard practice, not edge cases. The incidents in this report show how ransomware now creates sector-wide disruption rather than isolated IT outages.
What these attacks share is not a single malware family, but repeatable behavior patterns. Threat actors reuse access brokers, infrastructure, negotiation playbooks, and even each other. Tracking these overlaps is critical for understanding risk before an attack reaches the encryption or extortion stage.
This is where SOCRadar becomes relevant:
- Threat Actor Intelligence maps ransomware groups, affiliates, and their relationships across campaigns, helping teams understand who is working with whom.
- Dark Web Monitoring tracks victim listings, data samples, and early leak-site activity linked to known actors.
- Vulnerability Intelligence connects exploited CVEs with active ransomware groups, allowing teams to prioritize exposure based on real attacker behavior.
- Supply Chain Intelligence highlights third-party breaches and access sales that often precede large-scale ransomware events.
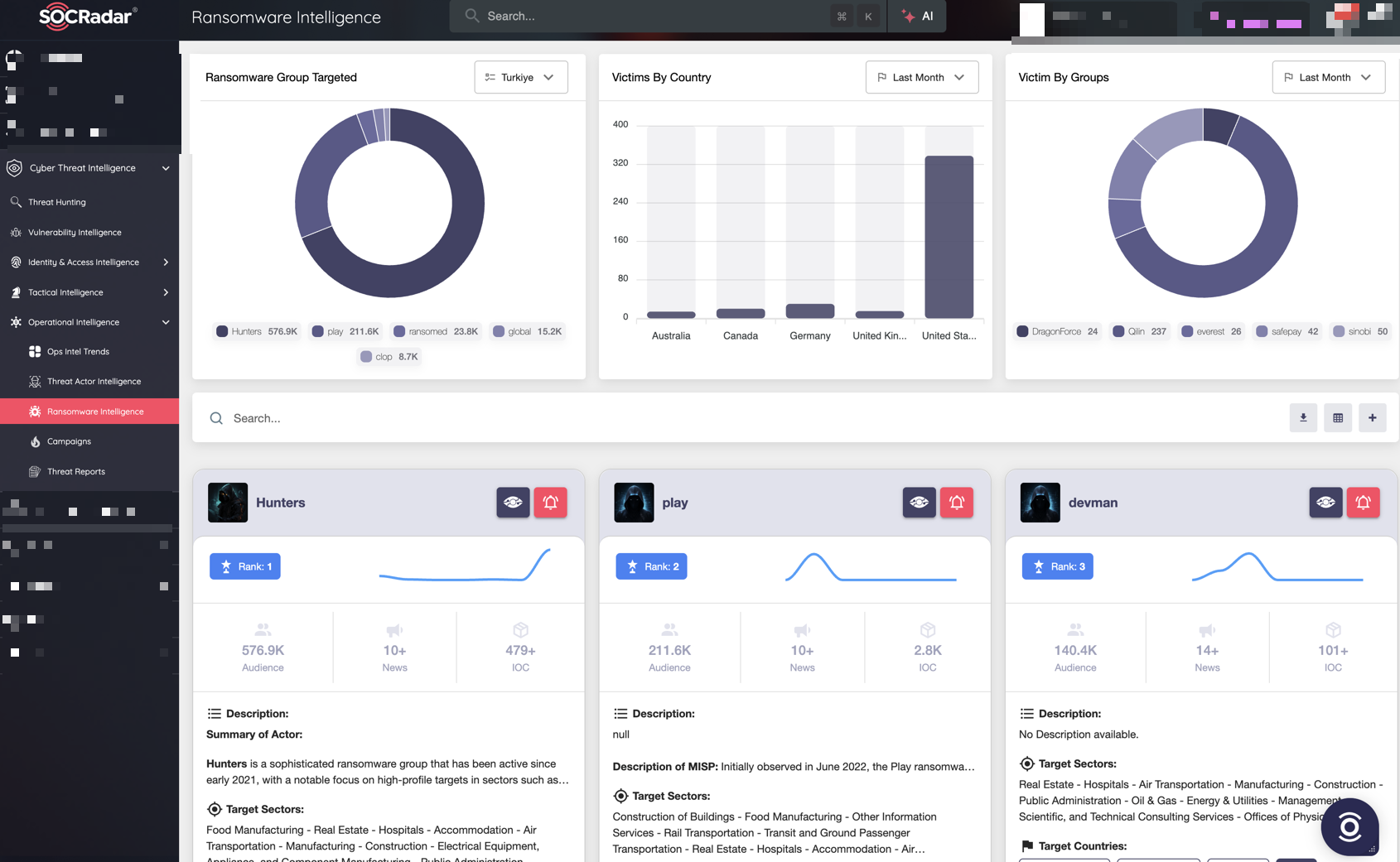
SOCRadar Threat Actor Intelligence
As organizations move into 2026, the challenge is no longer identifying the next ransomware name, but recognizing attacker behavior early enough to limit impact. Groups will continue to rebrand and collaborate, but their tactics leave signals. Organizations that can see those signals first will be better positioned to disrupt attacks before they turn systemic.
Article Link: https://socradar.io/blog/top-10-ransomware-groups-2025/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics


