Top Nation-State Cyber Threats Targeting the United States
Top Nation-State Cyber Threats Targeting the United States
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Most cyber risk in the United States starts with something simple: stolen data and stolen access getting traded for profit. In SOCRadar’s 2026 U.S. Threat Landscape Report, selling made up 70.76% of observed Dark Web activity. In other words, attackers kept feeding a marketplace where credentials and entry points move quickly from one hand to another.
That matters because it shapes the environment nation-state operators work in. They do not need to “invent” new entry paths when the underground economy already supplies access, phishing kits, and infrastructure at scale. At the same time, the motives diverge. Many criminal crews chase payment, but state-linked groups often chase long-term visibility: the inboxes, identity systems, telecom environments, and third-party pathways that influence decisions, expose relationships, or enable quiet persistence.
This post focuses on that second category. It breaks down the state-linked clusters most worth tracking, what they typically target in the United States, and the patterns behind how they run these operations.
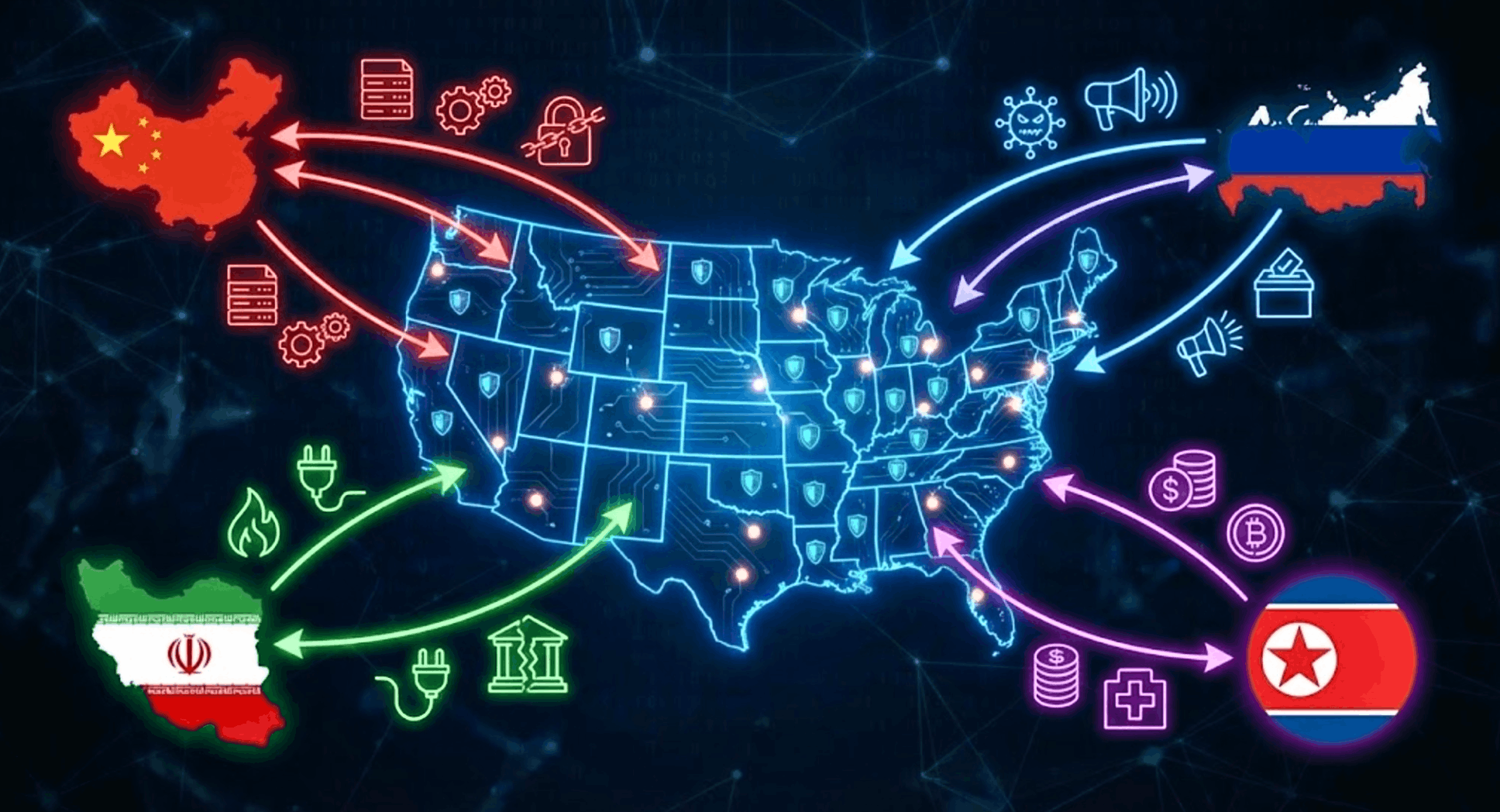
Nation-state threats targeting the U.S.
For wider U.S.-specific context beyond nation-state activity, SOCRadar’s 2026 U.S. Threat Landscape Report also covers the most targeted industries, how threat actors monetize stolen data and access, and how ransomware, phishing, and DDoS continue to pressure U.S. organizations.
China-Related Espionage and Long-Dwell Access
China-nexus operations tend to prioritize intelligence collection, persistent access, and strategic positioning inside communications and government-adjacent environments. In practice, that often means targeting email, identity, and infrastructure that enables downstream visibility into sensitive conversations.
Salt Typhoon
Salt Typhoon became a widely cited example of access that matters rather than smash-and-grab theft: get inside the pipes, stay quiet, and collect.
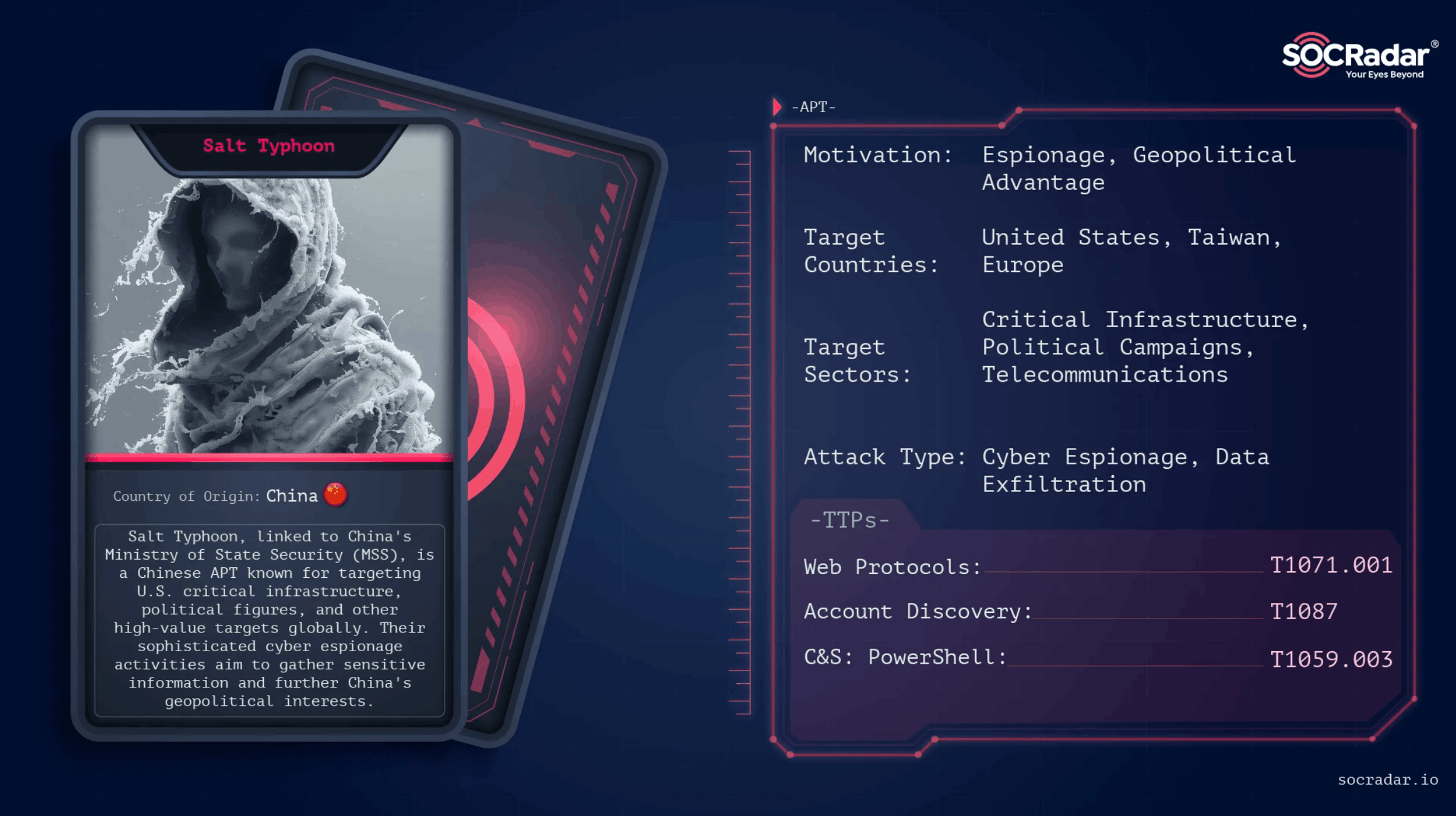
Threat actor card of Salt Typhoon
In January 2026, Salt Typhoon compromised email systems used by staff associated with major U.S. House committees, with uncertainty at the time about the depth of access and whether lawmakers’ emails were compromised.
A February 2026 Senate letter framed this activity as part of broader telecom security concerns and urged an oversight hearing with major carriers, including AT&T and Verizon. It also referenced FBI-reported scope, describing targeting of more than 200 U.S. organizations and activity spanning 80 countries, while citing reporting that the actors may have remained inside U.S. telecom networks.
A state-level advisory style recap from NJCCIC also summarized the committee-email targeting and reinforced the telecom-focused context.
How these operations tend to work
- Target the communications layer to gain strategic collection options (email systems, telecom environments, and the identity infrastructure around them).
- Prioritize persistence so access survives password resets and partial remediation cycles.
- Blend technical access with operational security, keeping activity low-noise and selective.
APT5
APT5 activity tied to U.S. and allied defense ecosystems showed a different but complementary approach: target people with believable context, including outside corporate controls.
A recent Google threat intelligence write-up described APT5 spearphishing campaigns that went after current and former employees of major aerospace and defense contractors, including messages sent to personal email accounts and lures aligned to targets’ roles, locations, and even personal interests. The same reporting emphasized that hiring and career-adjacent workflows can become a reliable pretext for targeting, especially when attackers impersonate recruiters, onboarding portals, or contractor brands.
How this maps to real U.S. exposure
- Personal email targeting reduces the value of corporate email gateways and security tooling.
- Highly tailored lures increase click-through rates, especially when the content looks like industry events, training, or job-related messages.
Russia-Linked Espionage Against Logistics and Strategic Enablers
Russia-linked campaigns in this period highlighted a familiar pattern: focus on sectors that enable military or geopolitical objectives, then use credential-centric tactics to move laterally through trusted relationships.
GRU Unit 26165 (aka APT28)
May 2025 joint cybersecurity advisory on CISA described a Russian state-sponsored campaign attributed to GRU unit 26165, tracked widely as APT28, targeting Western logistics entities and technology companies. The advisory said the campaign used tactics including password spraying, spearphishing, and manipulation of Microsoft Exchange mailbox permissions.
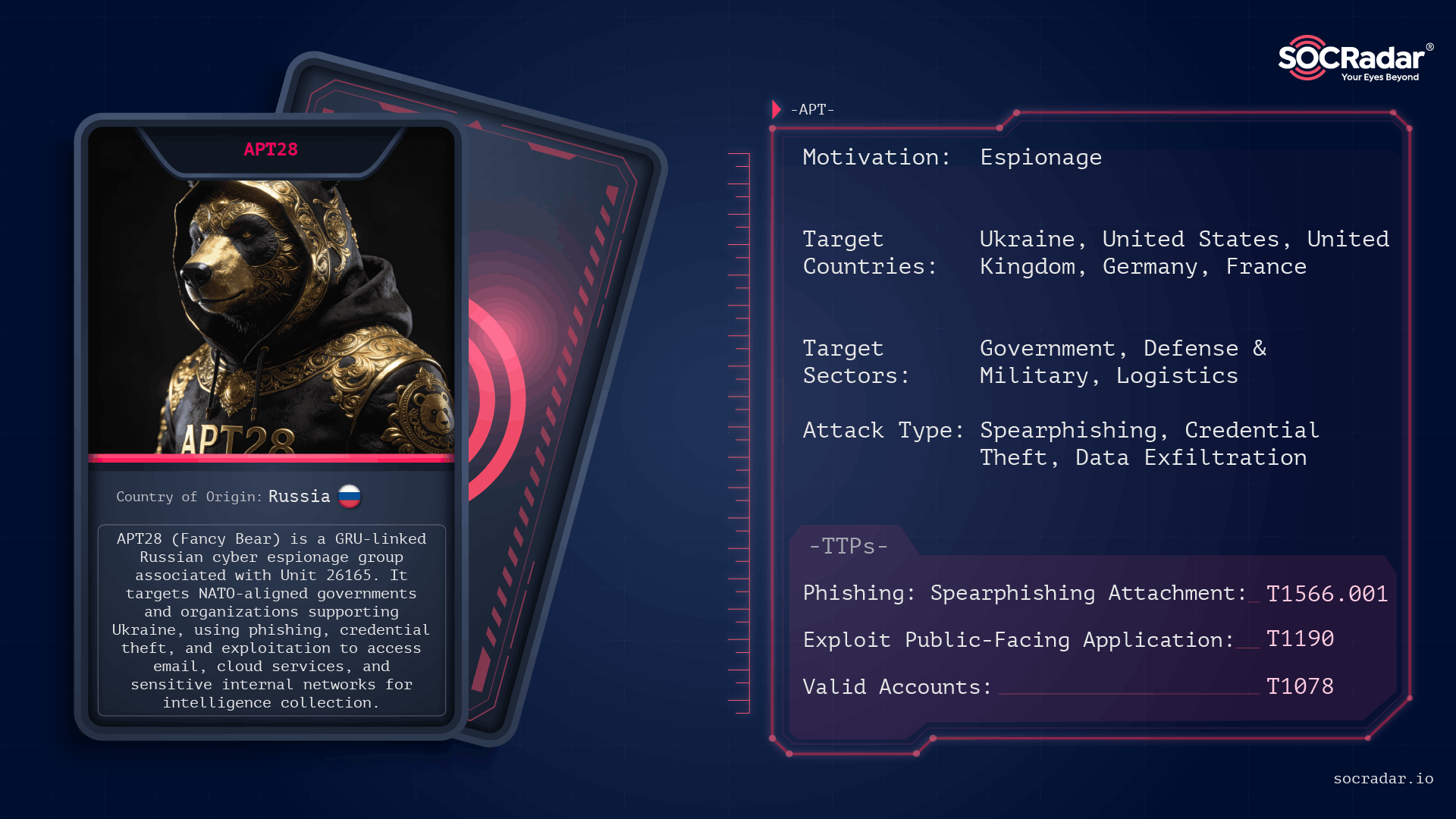
Threat actor card of APT28
While the advisory emphasizes Western logistics broadly, the operational implications for U.S.-based organizations are clear: logistics, IT service providers, and defense-adjacent supply chains remain high-value targets because they offer visibility and leverage across many downstream networks.
Common operational goals
- Espionage against movement, coordination, and support functions tied to defense and allied activity.
- Access expansion via trust relationships, using supplier or partner connectivity as the path to larger targets.
Russia-Linked Targeting of Defense Sector Personnel
Other campaigns linked to Russian intelligence spoofed the websites of hundreds of defense contractors and used job and recruitment-adjacent lures. This approach lets operators reach targets outside corporate networks by impersonating familiar brands and processes, then funnel victims into credential-harvesting pages, malicious document downloads, or malware delivery chains.
Google’s defense-sector write-up mentions other Russia-nexus activity affecting defense-related targets, including clusters such as APT44 (Sandworm) and UNC5792, as well as pro-Russia hacktivist operations that can amplify pressure through doxxing and disruptive campaigns. For U.S. defense-adjacent organizations, the risk extends beyond a single compromise because stolen credentials and footholds can be reused to pivot into partner ecosystems, subcontractors, and shared service providers.
North Korea-Linked Espionage and Revenue Operations
North Korea-linked activity spans classic intelligence collection and revenue generation, sometimes blending both. The most consistent U.S. risk is that operators target the people and systems around defense, policy, research, and remote access.
Kimsuky and QR-Based Spearphishing
The FBI FLASH published on January 8, 2026, described Kimsuky’s use of malicious QR codes embedded in spearphishing aimed at U.S. entities, particularly NGOs, think tanks, academia, and government organizations connected to North Korea issues.

Threat actor card of Kimsuky
The alert explains why QR-based lures are effective: they can push the victim onto a mobile device and bypass common email security inspection, then route the victim through attacker-controlled infrastructure toward credential harvesting pages impersonating common identity services.
Security media coverage also amplified this advisory for a broader audience, reinforcing that defenders should expect the technique to spread.
What defenders should take from this
- QR code phishing is not low-tech. It is a practical way to evade controls and steal identity access at scale.
- The target set includes policy and research communities that often have privileged access to sensitive conversations.
North Korean IT Worker Operations
Reporting and analysis in early 2026 highlighted North Korean use of impersonated recruitment workflows and remote IT worker schemes, including claims that North Koreans obtained roles across many U.S. companies as part of revenue operations.
We also previously detailed how the same playbook was used to infiltrate global hiring pipelines in our blog: “How Are North Korean IT Workers Hacking the Global Remote Job Market?”.
Even when these operations look HR-related, they introduce a direct access risk: credentials, VPN access, code repositories, and internal documentation can all become available to an adversary through normal onboarding processes.
Iran-Linked Credential Theft Through Hiring and Supplier Access
Iran-linked operators frequently lean into social engineering and the trust built into hiring and vendor relationships. The upside for them is clear: credentials and access paths can be cheaper and quieter than exploiting hardened perimeter systems.
UNC1549
The Google threat intelligence report described the Iran-nexus group UNC1549 using spoofed job portals, fake job offer lures, and other recruitment-themed artifacts to target aerospace and defense personnel. It also described follow-on activity that leveraged trusted third-party relationships for initial access.
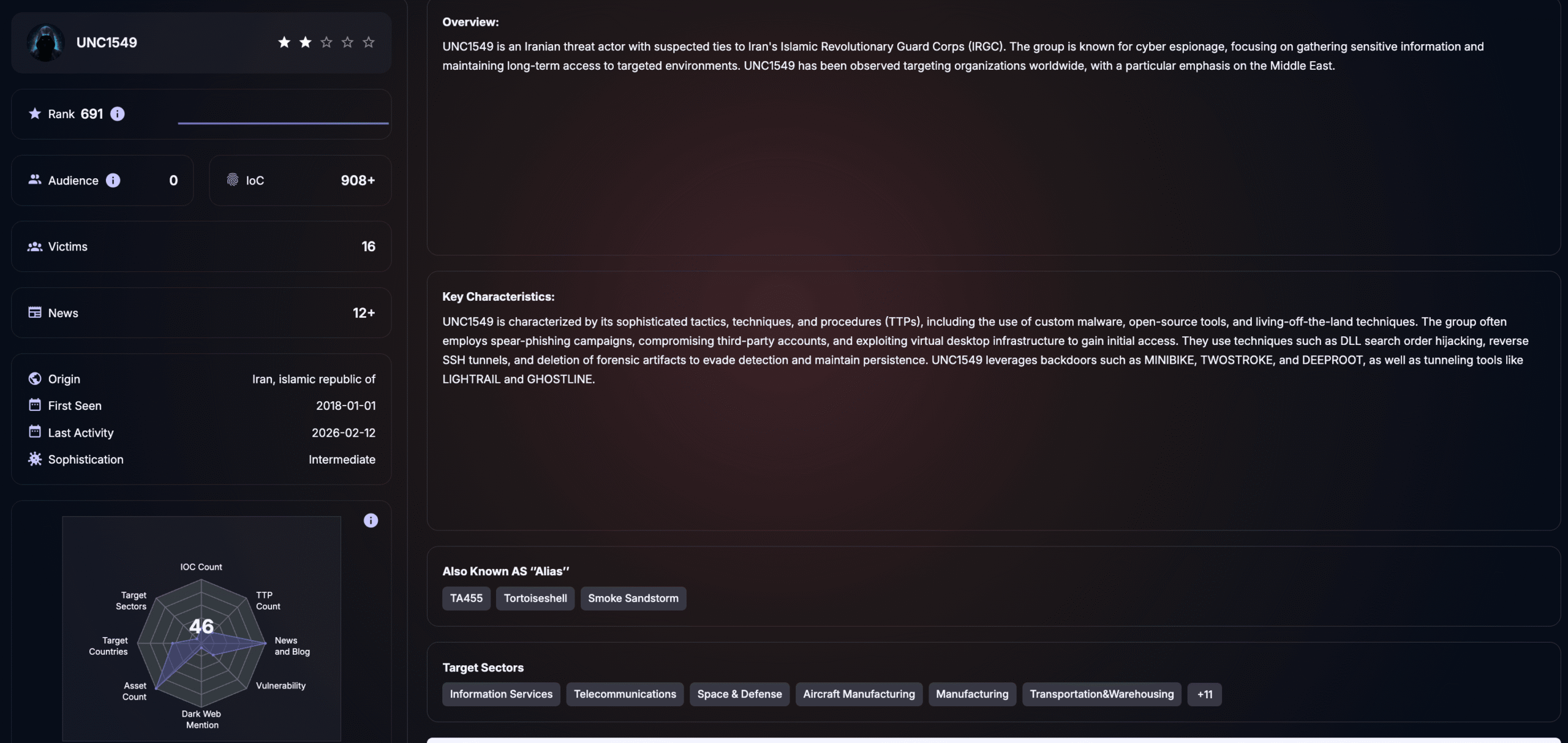
Threat actor overview of UNC1549 (SOCRadar Threat Actor Intelligence)
The report outlines a familiar post-access sequence: privilege escalation by targeting IT staff, and use of legitimate remote access services as part of the intrusion chain.
UNC6446
Google also described UNC6446 using resume-builder and personality test applications to deliver malware to targets in aerospace and defense, including targeting across the U.S. and the Middle East.
This reinforces a key point: if an adversary can weaponize normal career workflows, they can reach high-value personnel without fighting through a corporate security stack first.
How to Stay Alert & Reduce Exposure to Nation-State Threats?
These campaigns can look very different on the surface, but most of them converge on a few control points. If you reduce risk there, you reduce risk everywhere.
Harden identity and reduce session hijack value
- Require phishing-resistant MFA where possible and prioritize protections for cloud admin roles.
- Monitor for mailbox rule changes, suspicious OAuth grants, and abnormal logins tied to travel, new devices, or atypical user-agents.
Treat personal email and mobile as part of the enterprise threat model
- If staff handle sensitive work, personal inbox compromise becomes a corporate problem.
- Apply mobile device controls for high-risk roles and educate users on QR-based lures and recruitment document bait.
Reduce third-party and supply-chain attack surface
- Assume adversaries will pivot via suppliers and trusted connections.
- Maintain an accurate map of externally exposed services and remote access paths.
How Can SOCRadar Help?
- Attack Surface Management helps teams continuously inventory internet-facing assets and find exposed services that increase the chance of nation-state initial access, including forgotten portals and misconfigurations that get swept up in large-scale targeting.
- Cyber Threat Intelligence supports faster triage by correlating actor reporting, indicators, and observed tactics, helping analysts prioritize which alerts matter when a campaign like quishing (QR phishing) or committee-targeted espionage hits the news.
- Brand Protection and Dark Web Monitoring modules can add visibility into leaked credentials, employee-targeting chatter, and downstream exposure patterns that often show up before an intrusion becomes obvious.
SOCRadar’s Dark Web Monitoring, Black Market
- Supply Chain Intelligence helps teams understand third-party risk by assessing vendor exposure, tracking vulnerability status and incidents tied to suppliers, and surfacing early-warning signals when adversaries use partner ecosystems as a stepping stone.
SOCRadar’s Supply Chain Intelligence, Third-Party Companies
Conclusion
Nation-state operations targeting the United States in 2025 and 2026 did not just get louder. In many cases, they got smarter about where defenders tend to relax. Instead of breaking down the front door, the operators who matter most often aimed for the keys: identities, inboxes, and the “normal” business processes that slip past security muscle memory.
- China-linked activity kept circling communications and access layers because that is where long-term visibility lives.
- Russia-linked operators kept playing the trust game: if they can compromise an enabler like a logistics partner, an IT provider, or a shared identity, they can reuse that access again and again.
- North Korea and Iran reminded everyone that you do not always need sophisticated exploits if you can make the workflow do the work. Because a QR code that pushes someone onto mobile or a convincing hiring portal can be enough if it captures the right credentials.
Beyond these threats, if you want a focused look at how automation and AI are changing attacker speed and scale toward U.S. targets, see our companion post: “AI-Driven Threats Targeting U.S. Organizations.”
For defenders, the takeaway is clear: treat identity as the front line, assume attackers will reach employees outside corporate networks, and shrink the attack surface that makes persistent access possible. With consistent exposure management, strong identity controls, and intelligence-led prioritization, organizations can make these campaigns more expensive to run and easier to detect before they turn into strategic compromise.
Article Link: https://socradar.io/blog/nation-state-cyber-threats-target-united-states/
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics


